Evaluating network tokens: Webinar Q&A
Network tokenization promises better authorization rates, reduced fraud, and enhanced security, but implementing it comes with real questions.


Every online payment starts on the client side, where the cardholder enters the primary account number or PAN, expiration date, CVV, and other payment information. From that moment, the goal is to keep the data unreadable to anyone unauthorized to view it.
Encryption becomes the payment flow’s safety net against data breaches and credit card fraud. Under PCI DSS v4.0, cardholder data must be rendered unreadable, whether it sits in a database or travels between systems.
Satisfying these rules goes well beyond pure cryptography. Teams must use approved algorithms, rotate keys, and prove (through logs, assessment questionnaires, and other compliance forms) that each control is effective.
Evervault designs its platform with these controls in mind. Drawing on years of experience protecting payment data at scale, this article compares standard encryption with Evervault’s approach.
We’ll examine how standard encryption works, where it strains security teams, and how Evervault addresses those gaps. Let’s begin.
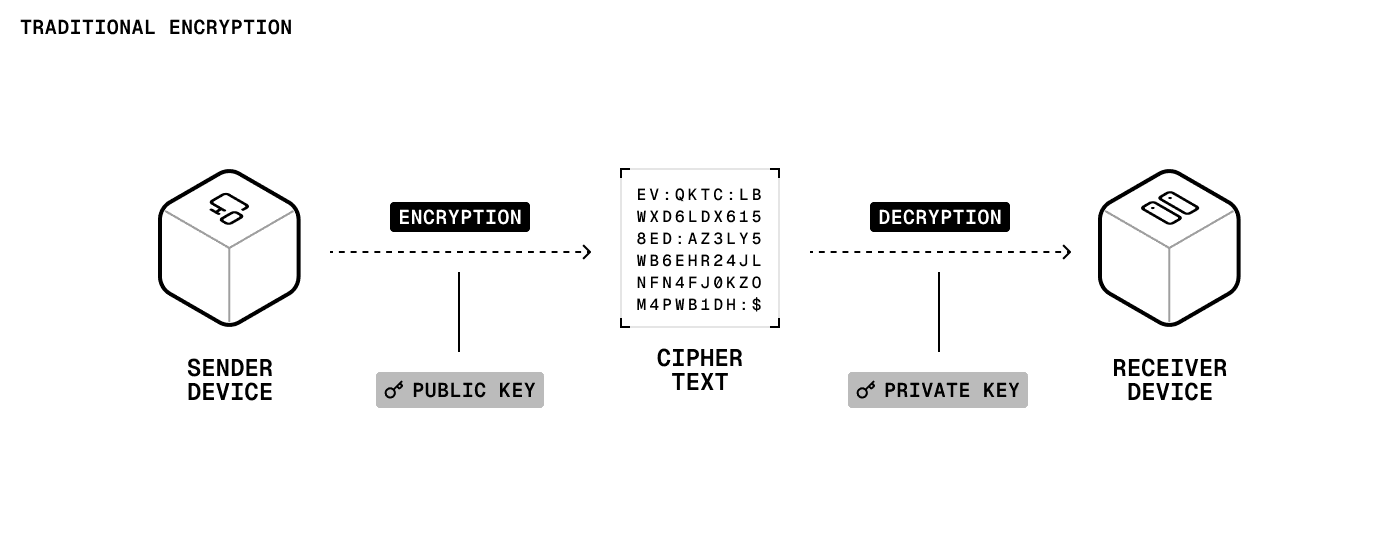
Traditional payment flows rely on proven data encryption algorithms: AES-256 secures stored data, while Diffie-Hellman (or an elliptic-curve variant) handles key exchange.
These standards align with what major credit card companies expect to accept payments during online checkouts.
The hard part is key management. Engineers must generate new keys, perform scheduled rotations, and prove that no single administrator can both retrieve and apply a key.
The system is exposed if keys drift into environment variables or weak authentication methods. Rotations make matters worse. Every new key forces a re-encryption of historical data, and multiple versions of each encryption or decryption key must be managed in parallel.
Traditional encryption methods protect payment systems, but they leave engineering teams carrying the load. They must thread encryption into every service and maintain detailed documentation to pass PCI compliance audits for their specific PCI compliance levels.
These pain points have set the stage for encryption-as-a-service. Evervault shifts the cryptographic heavy lifting into a managed enclave without limiting how developers structure their payment flows, payment processing, or payment gateway integrations.
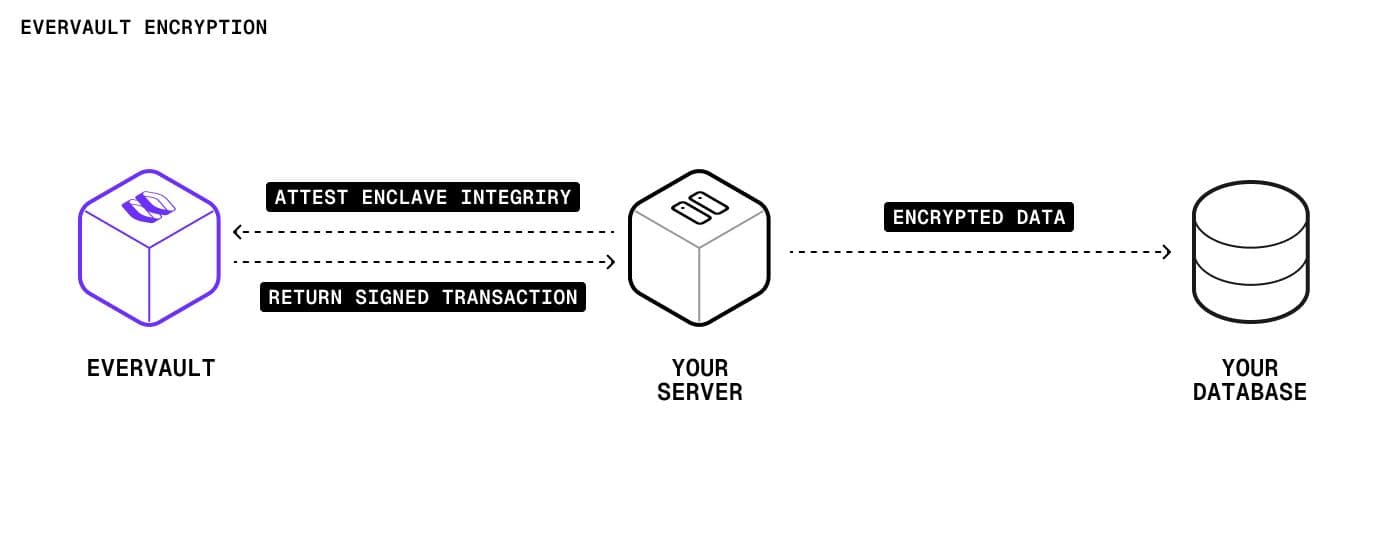
Evervault lets you integrate payment security with a single SDK call or by routing traffic through Relay, a reversible proxy between the client and downstream services. The Evervault Encryption Engine (E3) performs all cryptographic work within AWS Nitro enclaves, which are inaccessible to even Evervault employees.
Here’s how it works:
Put simply, Evervault packages PCI-compliant, field-level encryption into a consumable API that works across different payment methods. Its dual-custody design lets teams hold only ciphertext locally while retaining end-to-end control over the payment pipeline.
Now that we’ve covered the encryption solutions, let’s break down the key differences between traditional workflows and Evervault’s service.
We’ll compare them across four areas.
Engineers need to enable encryption in the browser, the API layer, the database, and every batch job in between. Any change in ciphers or compliance rules multiplies the maintenance work.
A single SDK call or Relay endpoint swap encrypts data at capture. Key exchange, AES-GCM settings, error handling, and all of the other heavy lifting are abstracted within Evervault’s service.
A cloud KMS (Key Management System) or an HSM (Hardware Security Module) is simple—until rotation day. Keys must be split across custodians, re-encrypted in live databases, and updated with near-zero downtime.
Keys stay inside the Evervault Encryption Engine (E3), isolated in AWS Nitro enclaves. Shamir Secret Sharing fragments the master key, and E3 handles rotations upon customer request.
TLS protects data in transit, but plaintext still touches application servers prior to further encryption, creating an attack window.
Client-side encryption happens immediately via the public key or at the edge through Relay (for server-side data). As a result, only the ciphertext reaches storage.
In-house servers handle decryption, so the application itself becomes part of the Cardholder Data Environment (CDE). A single data breach (or lapse in physical access controls) to those servers by malicious software can turn sensitive cardholder information into stolen data.
Plaintext lives only inside a Nitro enclave. Relay decrypts just long enough to inject the card number into a trusted outbound request, then wipes the memory, leaving no card data in the app layer.
Because the app stores raw card data, developers must satisfy every control set by the PCI Security Standards Council (including segmentation, file integrity monitoring, incident response, threat detection, annual self-assessment questionnaires, and more). These must be documented for qualified security assessors.
Many of those controls shift to Evervault’s audited infrastructure. The SDK aligns with PCI DSS v4.0, which helps lighten the operational checklist.
The differences are summarized below:
| Area | Traditional Encryption | Evervault Encryption |
|---|---|---|
| Developer Experience | Lives in the browser, APIs, DB, and batch jobs; any cipher or compliance change echoes everywhere. | One SDK import or Relay swap encrypts at capture; heavy lifting and error handling are abstracted, simplifying payment systems. |
| Key Management | KMS/HSM rotation means splitting keys across custodians and re-encrypting live data with minimal downtime. | Keys stay in the E3 Nitro enclave, fragmented via Shamir Secret Sharing; Decryption key is shielded from developer exposure. |
| Encryption at Capture | TLS covers transit, but plaintext still reaches the server first (leaving an exposure window). | Browser or Relay encrypts before data leaves; only cipher text ever hits storage (securing financial transactions at the source). |
| Decryption Environment | In-house decryption keeps the app in scope as the CDE (Cardholder Data Environment). | Decryption happens inside the Nitro Enclave; memory is wiped immediately, so the app never sees raw cardholder data. |
| PCI DSS Compliance | Dev teams own the full PCI DSS control set (segmentation, FIM, incident response, etc.). | Many controls shift to Evervault’s audited infrastructure; the SDK is built to satisfy PCI DSS v4.0. |
Evervault moves encryption and key management into a dedicated platform that aligns with PCI DSS requirements. The main benefit is its dual-custody design, which keeps raw cardholder data away from the stack.
The result is a safer, more adaptable security payment system. Teams can change payment processors, launch in new regions, or add subscriptions without having to manage keys or deal with PCI rules.
The flexibility translates into concrete use cases like:
Modern payment stacks, secure payment systems, and third-party vendors can’t afford to think of data protection as an afterthought. By moving the heaviest cryptographic and operational tasks into a managed enclave, Evervault shows one practical path to PCI DSS compliance.
For engineering teams, the next step is due diligence. Think about your current security posture and whether it's worth offloading some of the operational load. Consider where your plaintext lives, how often keys are rotated, and whether your current security measures can keep up as you scale.
If you want to learn more about how Evervault handles payment card data and security issues, check us out here.
Use Evervault’s developer-friendly security infrastructure to collect and reveal cards, optimize your payment routing, and comply with PCI DSS.
Learn more