- January 10, 2024
Introducing Confidential Computing, powered by Evervault Enclaves

Tl;dr - we’ve built a great product for confidential computing, go try it.
Today, we’re delighted to share our new Confidential Computing solution, alongside the general availability release of Evervault Enclaves.
Our mission is to make world-class data security and compliance effortless and accessible. Achieving this involves building powerful abstractions on market-leading security technology – making them easier to use, more secure, and more scalable.
After a several month beta program, we’re convinced that our Enclaves product has broken new ground – unlocking a new level of robust and accessible data security. We’re excited to mark this new era of data protection.
The Power of Confidential Computing
At Evervault, we believe that relying solely on perimeter defenses, like network firewalls, to stop cyberattacks is no longer enough. Hackers are getting smarter, and security can no longer be an afterthought. Having developed powerful solutions for protecting data at rest and in transit, we steered our attention towards the problem of data in use. This is where confidential computing can help—a game-changing form of data security that's hardware-enabled and completely isolated.
Many of the major cloud providers today offer confidential computing technologies, including AWS Nitro Enclaves, Intel SGX, AMD SEV, and Arm TrustZone. They offer raw confidential computing instances, which essentially create an isolated, super-secure space for you to process your most sensitive data. Think of it like a burglar breaking into your house, only to find every valuable thing you own locked in an indestructible vault buried deep, deep underground. Once implemented correctly, it’s the most secure way to process data.
Roadblocks to rapid enterprise adoption
While confidential computing is a big step forward in data security, there's a catch—many aren't tapping into its full potential because adopting it at an enterprise scale is a headache. To make it work, companies have to refactor their applications to work within the confines of confidential computing, a time-consuming process that requires in-depth subject matter expertise, and eats up lots of specialized developer hours. This hinders adoption, forcing companies to make the difficult tradeoff between rapid cloud innovation with increased security vulnerability, or slower, somewhat secure in-house options which puts them behind competitors in the market.
We’re addressing this dilemma in our latest release by making confidential computing incredibly easy to implement.
Accelerating a New Era of Data Security
Introducing Confidential Computing, highly constrained compute environments that allow you to easily run sensitive workloads. We’ve abstracted away the complicated bits and added stronger data protection, meaning that when you process sensitive data with Evervault, you can dramatically improve your security posture in minutes, not months.
We’ve done this by focusing on five core principles when designing our Confidential Computing solution (powered by our Enclaves primitive).
- Fully isolated by default - Network access, storage, and logging are explicitly enabled by you to guarantee that your sensitive data is only used for its intended purpose.
- Data is only decrypted within an enclave - Confidential computing ensures that any previously encrypted data can only be decrypted within the hardened security environment of the enclave.
- Code is verifiably authentic - Instantly guarantee your code hasn’t been tampered with. All workloads are fully attestable — applications you deploy are signed by you, and you can verify that requests are being sent to a signed enclave at runtime.
- Lift and shift any existing Dockerfile - The traditional security model of Confidential Computing can be hard to pair with a real-world application due to the lack of networking and limited observability. Enclaves makes it easy to import an existing application into a secure environment without jeopardizing security by supporting fine-grained controls on networking, and transaction logging.
- Compatible with each Evervault primitive - Enclaves work interoperably with our other products so it natively supports encryption and decryption of sensitive data by default.
By removing these obstacles to adoption, Evervault enables organizations to process and share sensitive data without compromising on security.
How to use confidential computing to enhance your security
Cryptographic Key Management
There are several popular use cases for Enclaves related to verifiable operations with cryptographic keys, like transaction signing. The traditional approach to handling transactions is that a developer might have a database (or a secure data store like HashiCorp Vault) containing private keys, which are then retrieved and used to sign transactions when required.
The problem with this approach is that there is a central store of private keys, and if that store was compromised, there is significant risk of monetary loss – and more generally, existential business risk. Unfortunately, there are countless examples of digital asset thefts from exchanges and service providers who had inadequate key security infrastructure.
Using Enclaves to address this provides an elegant, trustless solution for handling key operations. Developers can deploy an Enclave which accepts Evervault-encrypted private keys and transaction metadata as an input, and which returns a signed transaction as the result.
The Enclave is fully attestable, so you can guarantee that the only point at which the private key is decrypted is within a verified enclave which can only perform signing operations.
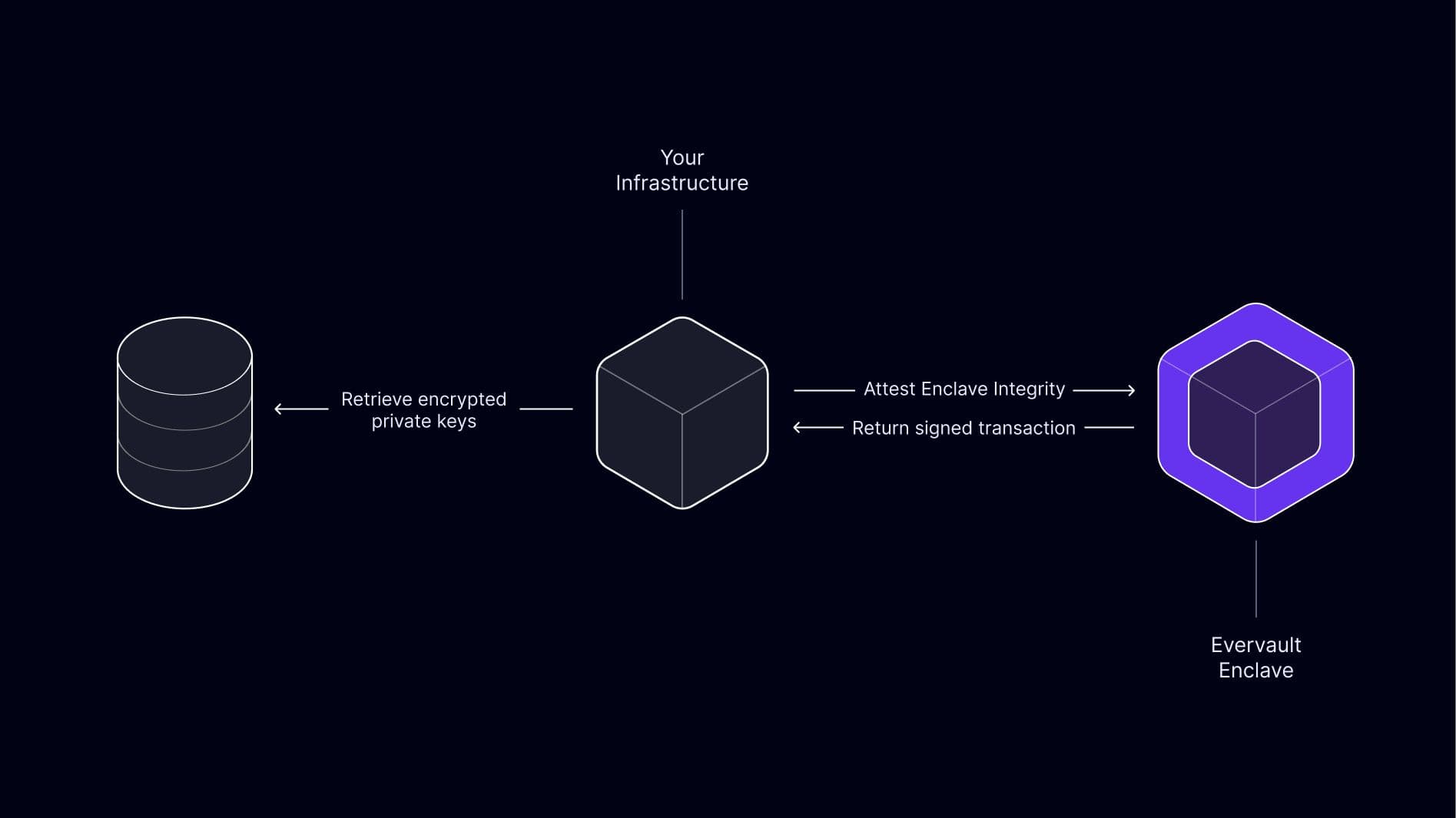
More broadly, Evervault Enclaves provide robust infrastructure for building novel key management flows, such as non-custodial or Multi-Party Compute (MPC) solutions. By supporting attestation, Enclaves are a perfect fit for an auditable and trustable central entity in an MPC scheme. Cooperating parties can audit the source code for a service, and reproduce the attestation measurements from source ahead of participating in a Multi-Party Computation.
Healthcare Data Sharing
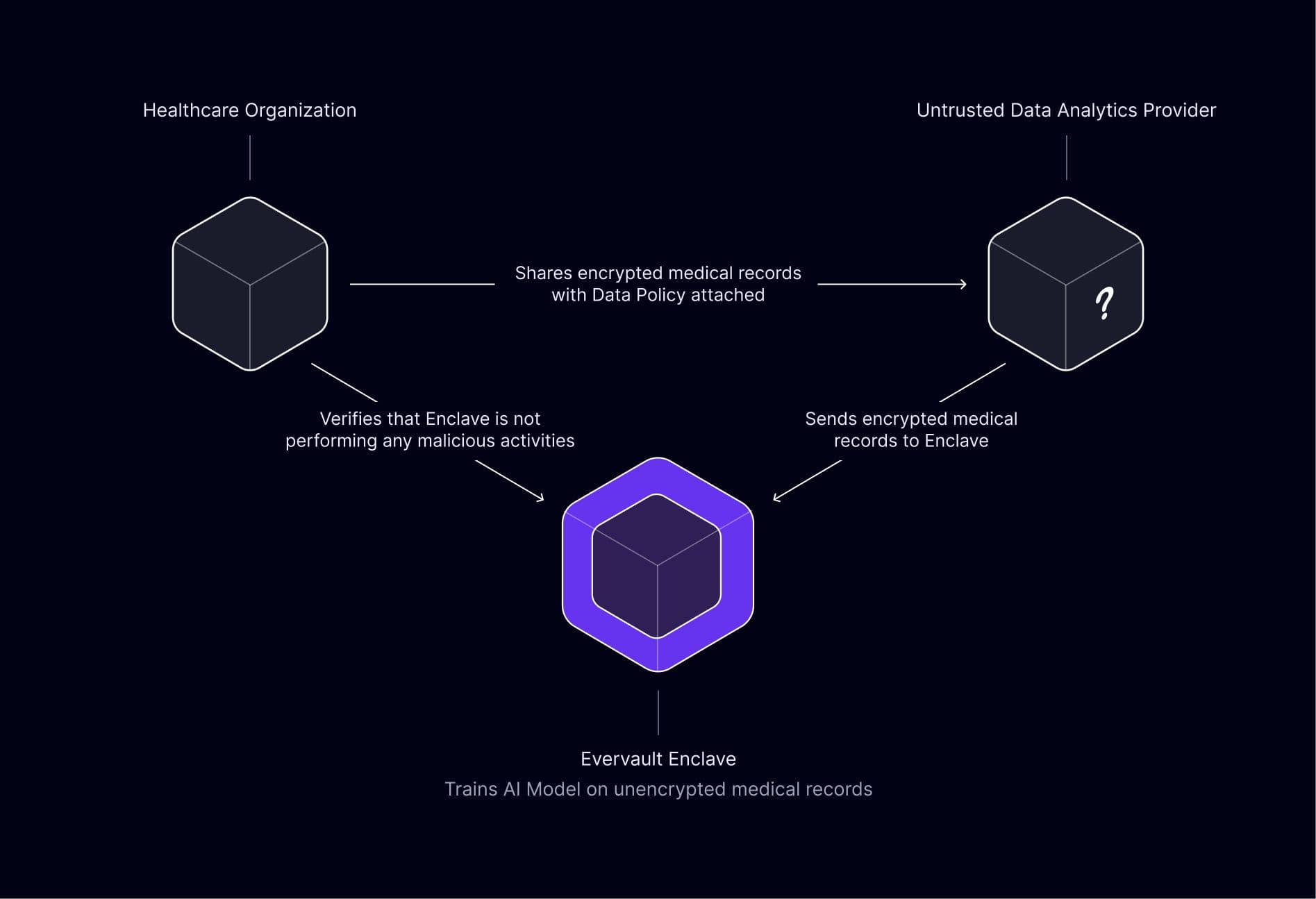
Let’s say a developer wanted to build software to share sensitive data, like medical records, with an untrusted third-party for data analytics. Medical records are extremely sensitive and subject to regulation like HIPAA in the US. As such, it would be wise to share the sensitive data with the third-party in a way that guarantees it can only be used for its intended purpose – to minimize breach risk and ensure compliance with regulation.
With Evervault, you can do this easily. By sharing encrypted data with the untrusted third-party, in combination with Evervault Data Policies, a developer could ensure that the medical records are processed only by a pre-approved Enclave. Any other attempts to decrypt or modify the data would fail.
Start securing your sensitive workloads
Evervault sees security as a crucial part of cloud computing, not an afterthought. This GA release of Enclaves marks an exciting step forward for data security.
If you’re curious, the easiest way to see if Enclaves works for you is to create a free Evervault account and take a look at our docs, or follow the link below to request a demo.
See if Evervault is right for your Confidential Computing use case
A simple solution to protect your critical workloads from unauthorized access and interference in the cloud.
Learn more

