Beyond payment tokenization: Why developers are choosing Evervault's encryption-first approach
How Evervault’s dual-custody encryption model eliminates the fundamental limitations of traditional tokenization for PCI compliance

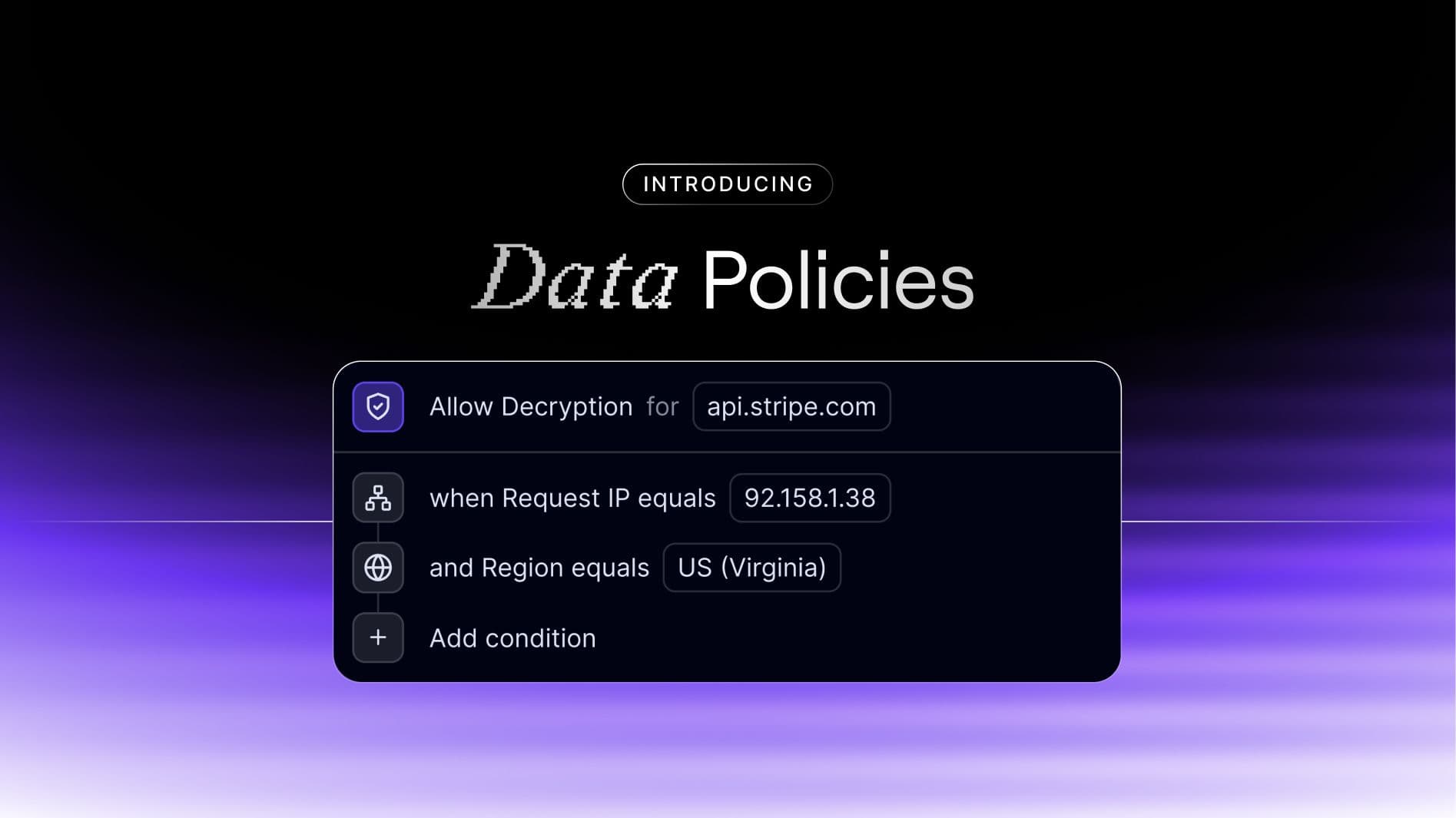
Introducing Data Policies, the newest feature in Evervault's core platform. Data Policies guarantee that when you encrypt sensitive data, that data can only be used for its intended purpose.
With Data Policies, your team can precisely control how sensitive customer data is accessed and decrypted by configuring specific qualifying conditions like request regions, timestamps, or IP addresses. Policies can be created to explicitly permit or forbid decryption, depending on the context of the decryption. These policies are embedded in the encrypted data at the time of encryption, ensuring that the data itself understands where and when it can be decrypted.
By incorporating this added functionality into Evervault's encrypted data workflows, the risk of data misuse is reduced, resulting in significantly hardened data security.
Traditionally, when encrypting sensitive data, either in-house or with a third-party vendor, the access to that data is defined by whoever has the key. When standard encryption keys are used, unauthorized access to both the key and encrypted data could result to the unlocking of all data — irrespective of its intended application or sensitivity.
While Evervault’s dual security model de-risks the chance of this scenario occurring, Data Policies provide a powerful new layer to guard against data misuse, both inside and outside your organization.
Data Policies are a set of a conditions that you establish, which determine how and when data can be decrypted. These can be based on a multitude of parameters such as the type of data, its geographical location, a timestamp, or specific user permissions.
Embedding granular permissions in the encrypted data itself ensures that even in the worst case scenario (your master API Key and your encrypted data fall into the wrong hands), your data remains unusable outside its intended purpose.
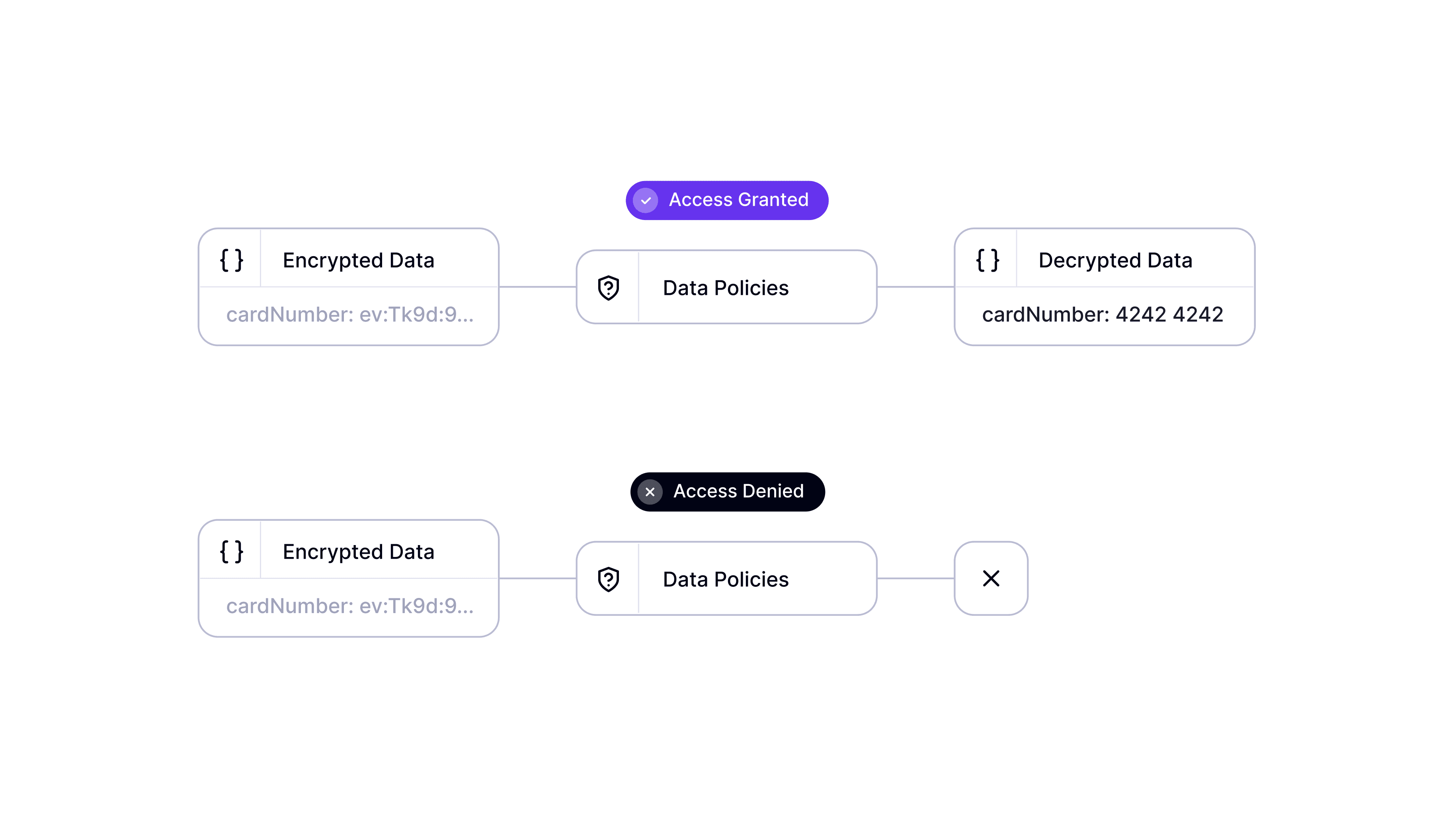
Embedding decryption conditions in encrypted strings allows Evervault users to construct a variety of hardened security workflows. Here are some examples of how of our early-access users have implemented Data Policies:
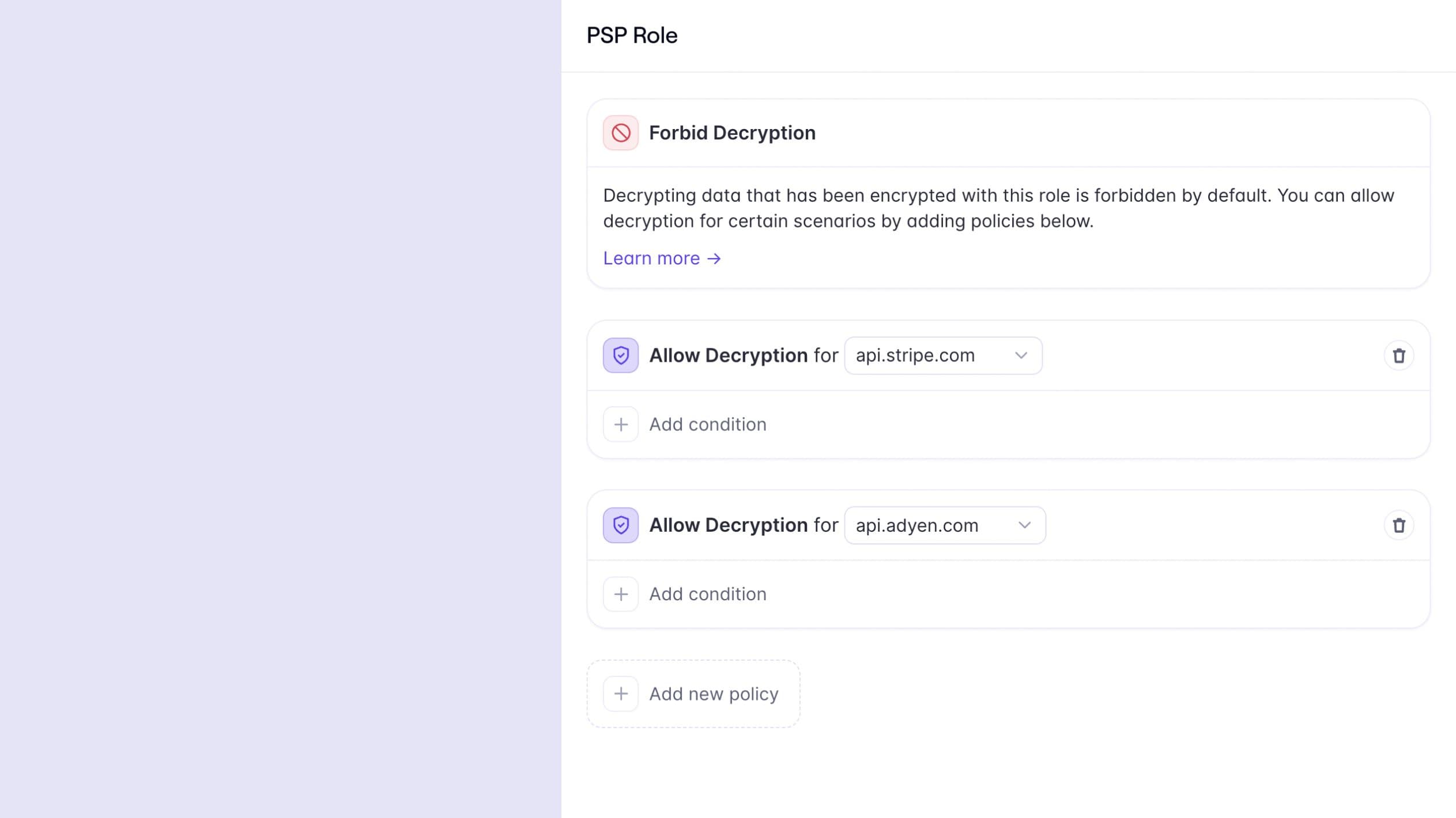
“I’m building a booking aggregator that processes payments using multiple PSPs for payment orchestration. I want to ensure that encrypted card numbers are only decrypted when my application processes a payment with Stripe or Adyen.”
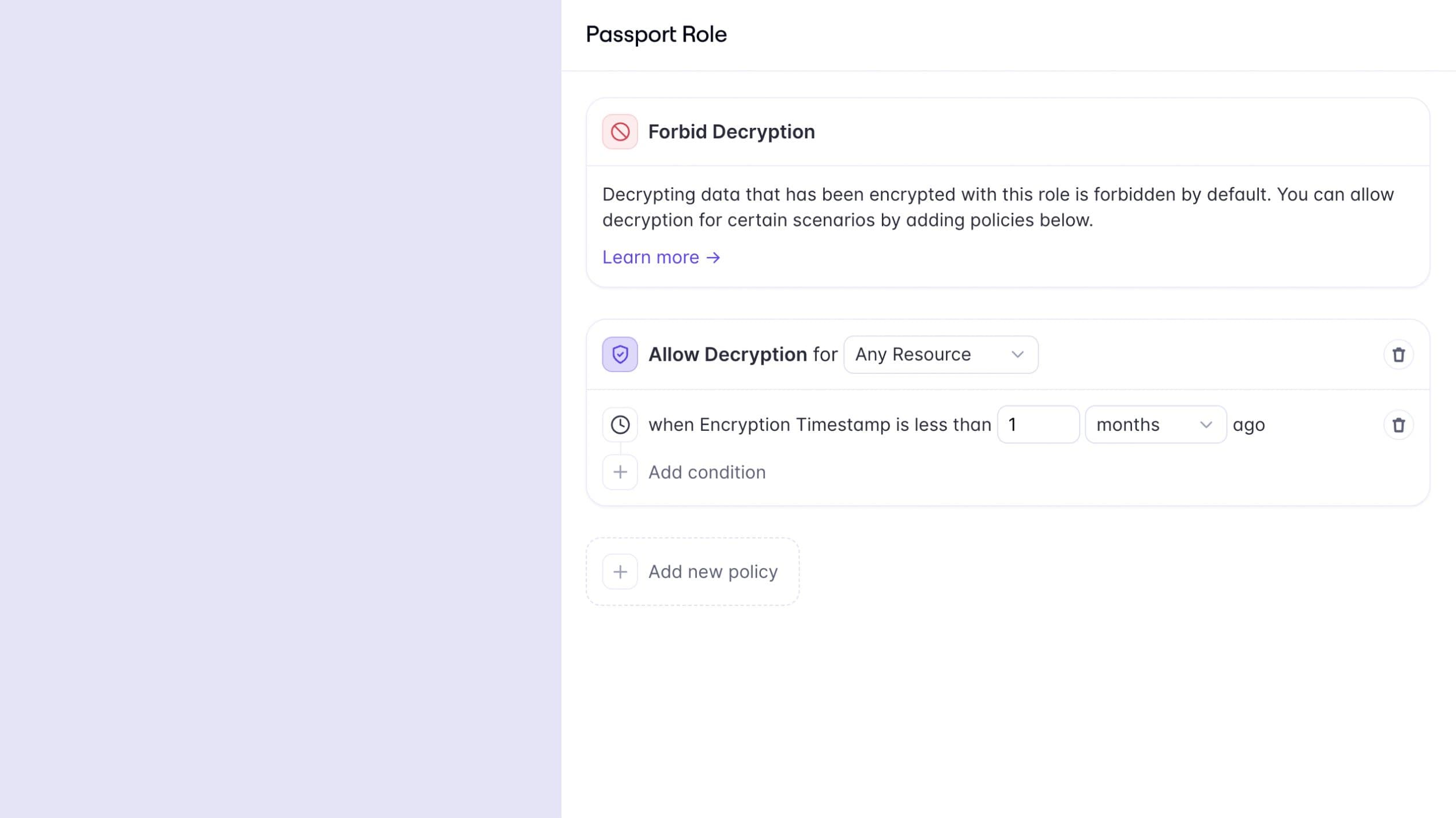
“I’m building a hospitality management platform and need to encrypt passport scans made when customers check in at hotels. I need to ensure that the hotel management dashboard can only access and decrypt the scans up to 1 month after check-in.”
“I’m building a mobile app that allows my users to create photo galleries. I want to allow them to link their Instagram account with my app to import their Instagram feed. I want to ensure encrypted Instagram’s OAuth tokens are only decrypted when my application consumes the Instagram API”.
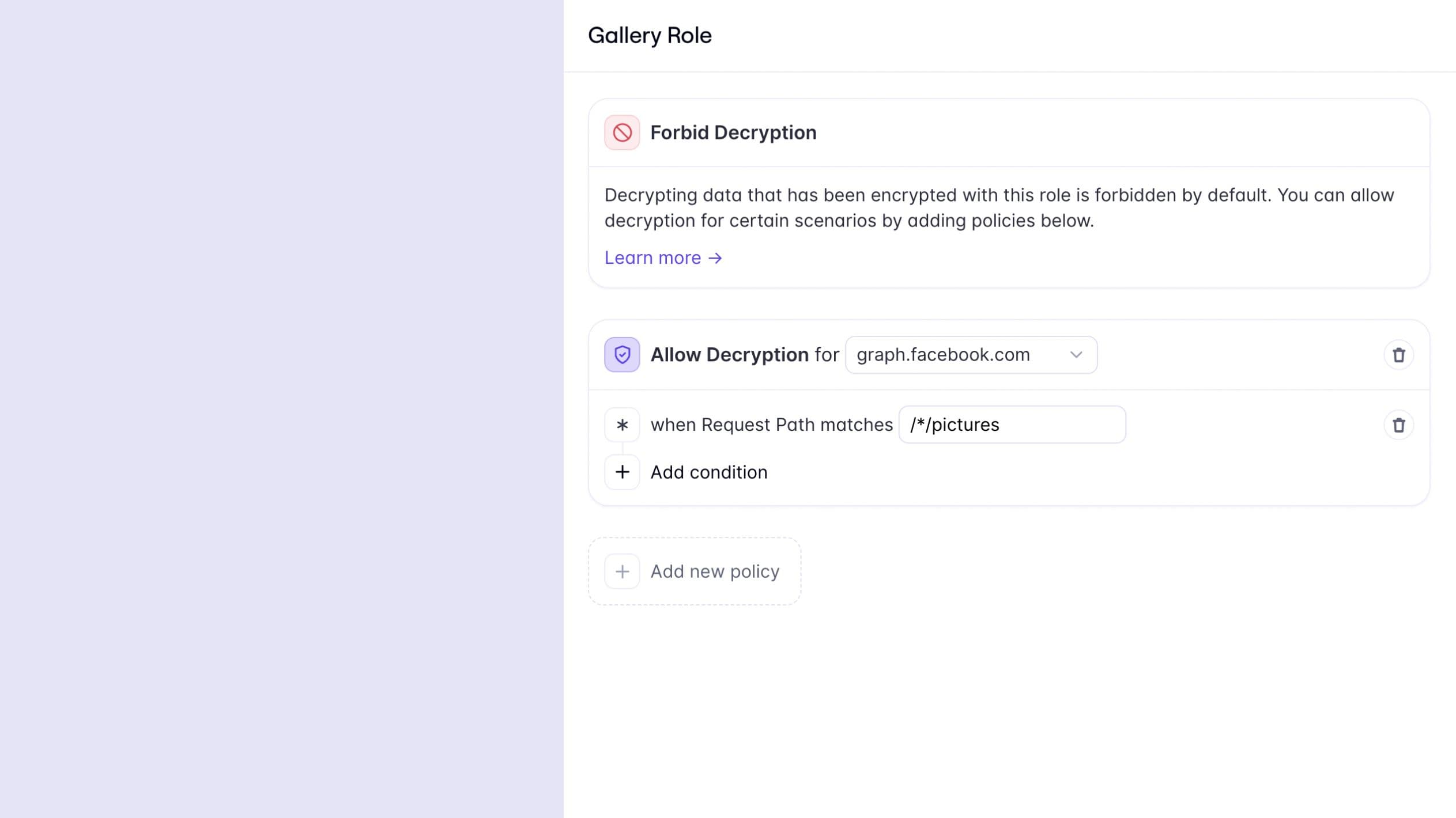
Data Policies is the latest addition to an array of easy-to-use features that enhance data security and ensure Evervault fits neatly into your existing infrastructure. Combined with capabilities like Audit Logging, Alerting, and User Access Control, the Evervault platform offers a robust framework for tackling complex problems related to security and compliance.
Ready to try it out? Create a free account and follow along in the data policies docs to get started.
Use Evervault’s flexible developer building blocks to keep your customers’ data secure and compliant at all times.
Get started