Evaluating network tokens: Webinar Q&A
Network tokenization promises better authorization rates, reduced fraud, and enhanced security, but implementing it comes with real questions.

Learn what ASV scans are, when you need them for PCI compliance, and how Evervault simplifies the process with a modern, user-friendly solution.
Read More
Network tokenization promises better authorization rates, reduced fraud, and enhanced security, but implementing it comes with real questions.

If you're responsible for payments infrastructure, you've probably heard conflicting advice about network tokens. Some vendors promise dramatic authorization rate improvements, while others downplay the benefits entirely.
How Evervault’s dual-custody encryption model eliminates the fundamental limitations of traditional tokenization for PCI compliance
Visa's 2025 Acquirer Monitoring Program (VAMP) represents one of the most significant changes to payment fraud monitoring in over a decade.

If you're a payment service provider working with high-risk merchants, April 1st, 2025 marked the beginning of a big change in how Visa calculates fraud rates.

During our 3D-Secure for high-risk payments webinar, attendees asked many insightful questions. To ensure everyone benefits from the discussion, we've compiled some key questions with our answers below.

Compare traditional encryption vs Evervault for payment security. Explore key management, PCI compliance, and data protection approaches for secure card processing.

Secure your payment pages against script and security header attacks while complying with PCI DSS 4.0 requirements, 6.4.3, and 11.6.1.
Every declined payment is a missed opportunity. Whether it’s a failed credit or debit card transaction or a false fraudulent transaction flag, each breakdown in the payment authorization process costs you revenue—and chips away at customer satisfaction.
For online merchants in the US, the modern version of 3D Secure offers a powerful upgrade to payment security.
Online fraud is rising in Japan, and new updates to the country’s Credit Card Security Guidelines mean businesses can no longer afford to delay stronger protections.
The key differences between network tokens and tokenization, including strengths and challenges alongside merchants and vendors.
During our Script Security webinar, we had some great audience questions pop up during the presentation. Here are the answers.
Up-to-date card authorization is vital for modern businesses, learn strategies to maintain customer trust and scale operations effectively.

As we head into 2025, here are five practical ways to boost your card authorization success rates.
EMV 3D-Secure represents a crucial advancement in online payment security, balancing robust fraud prevention with optimal user experience. This blog is for merchants considering implementing 3DS.
During our How to Implement & Optimize 3D-Secure webinar, we received a lot of insightful questions from the audience. To make sure everyone benefits from the discussion, we’ve compiled the top questions along with our answers below.
Understanding the technical fundamentals behind 3DS can guide better decisions about authentication flows, fraud prevention measures, and user experience optimization.

During our Network Tokens webinar, we had some great audience questions pop up during the presentation. Here are the answers.

Implementing card tokenization in 2025 is straightforward and versatile. It also remains a crucial step to enhance payment security and streamline compliance efforts.

Complete guide to implementing encryption for PCI Compliance in 2025. Understand must-haves and some practical strategies to maintain compliance.

Understanding the VISA chargeback rules and implementing an effective chargeback management strategy is essential for any merchant in 2025.

The most notable considerations for implementing 3D-Secure authentication in 2025

Get an understanding of what network tokens are, how they differ from traditional tokenization, and what you should think about when implementing them.
Multi-payment processor systems integrate multiple payment providers to handle transactions. Use Multi-psp to boost coverage to local populations and minimizes net transaction fees.
We've launched new payment extensions, 3D-Secure, account updater, and made many enhancements to our core product!
Unravel DORA’s encryption mandates and explore the evolving standards to ensure your company meets compliance by the 2025 deadline

Learn what 3D-Secure is, its pros and cons, and how you can implement it effectively

Flexible and universal API for 3DS authentication that works independently of your payment processor.

Today we’re launching our modular payments security platform, to give our customers greater flexibility and control over their payments stack.

A Business Guide to Simplifying Security
Synchronizing the Unsynchronized
A deep dive into how enclaves work
Building Enclaves presented various technical challenges, dig into our roadblocks with service discovery and how we’ve used Consul to fix it.
How we built our Enclaves primitive, we dig into our redesign of Enclaves egress networking with iptables.


How Evervault combined the best of defined and customized validation to achieve PCI DSS v4

Check out what's new in the Evervault product this month!

Accelerating a new era of data security by making confidential computing incredibly easy.

How moving to v4.0 presents an opportunity to rethink security.

There are two ways to tackle the latest PCI standard—a lift-and-shift approach and a ground-up reevaluation.

Our product highlights from the year.

By sorting tactics into “protection before” and “protection after”, security teams can build more robust programs.

Check out what's new at Evervault product this month.
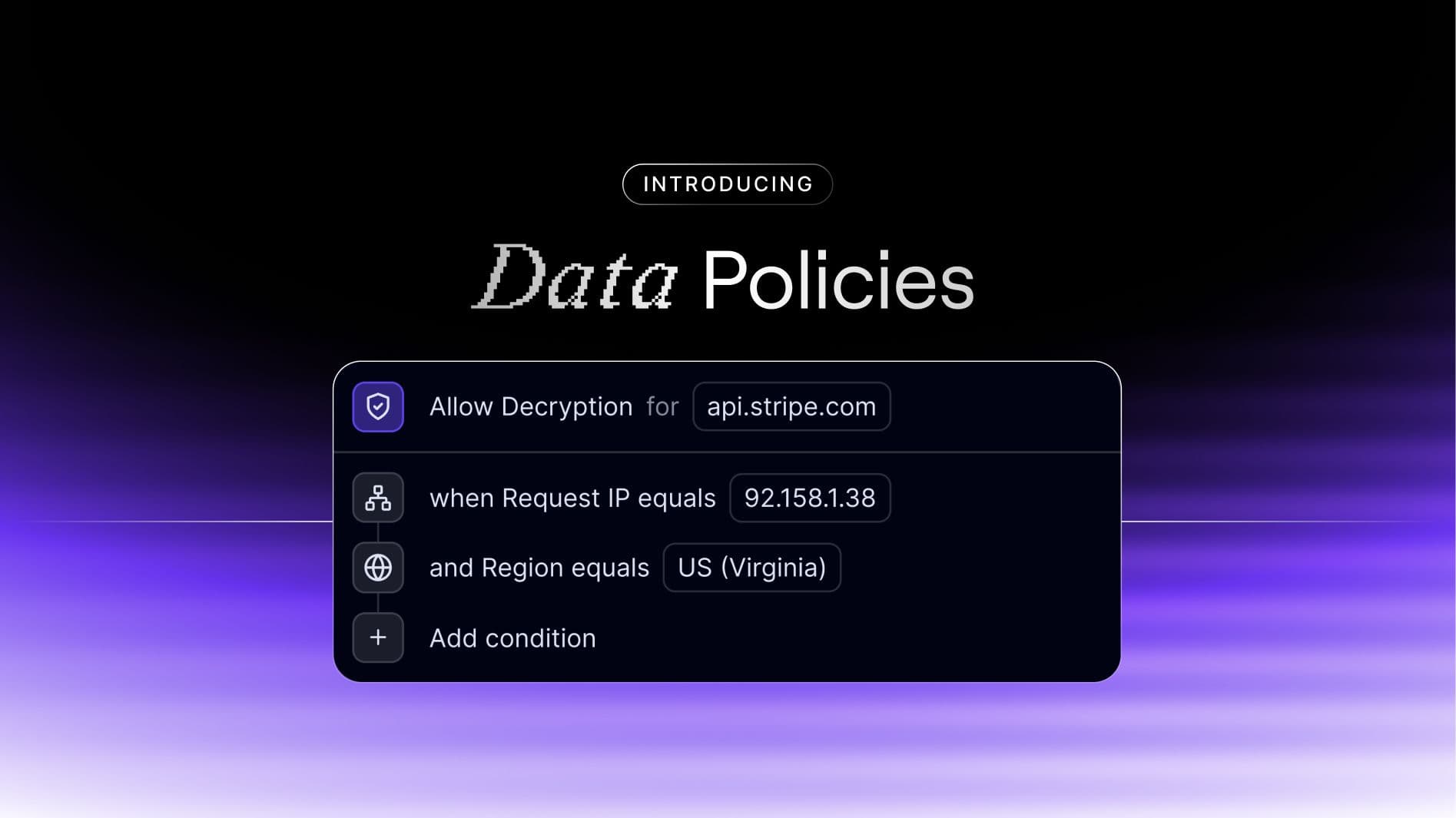
Introducing Data Policies, Evervault’s newest platform feature. Set clear rules that dictate how and when encrypted data can be decrypted.

His journey from founding a leading Node.js company to DevRel company Voxgig

How to think through protecting your company’s most important assets

Check out what's new within the Evervault product this month.

Modeling and mitigations for dealing with a malicious internal admin

Ensuring complete web3 wallet security through secure enclaves and encryption

The Hidden History and Politics of Encryption Algorithms

Companies often brag about encryption-at-rest? Is that really worth bragging about?

Empowering developers about security and privacy so they can implement measures from the start

Modeling and Mitigations of an External Attack.

What's new this month? Card Reveal, revamped PCI compliance and PII encryption solutions, and enhancements to Cages.

How empathy for the customer can supercharge your development

Third in our thread model series, we cover mastering cloud security.

“If you don't do security right, you can't have privacy.”
Modeling and Mitigations of Supply Chain Threats

From a co-founder turned engineer who is a self-described “security freak”

Multi-party computing has a lot of potential. Unfortunately, it’s rarely worth the hassle.

AI Privacy, Relay Redaction, and Decrypt API -- check out these and many more updates from this month

How to model system threats within a sample cloud-based stack, and a deep dive into mitigations for a potential malicious insider threat.

Establishing guardrails rather than gates, distinguishing signal from noise, and how security is about partnership.
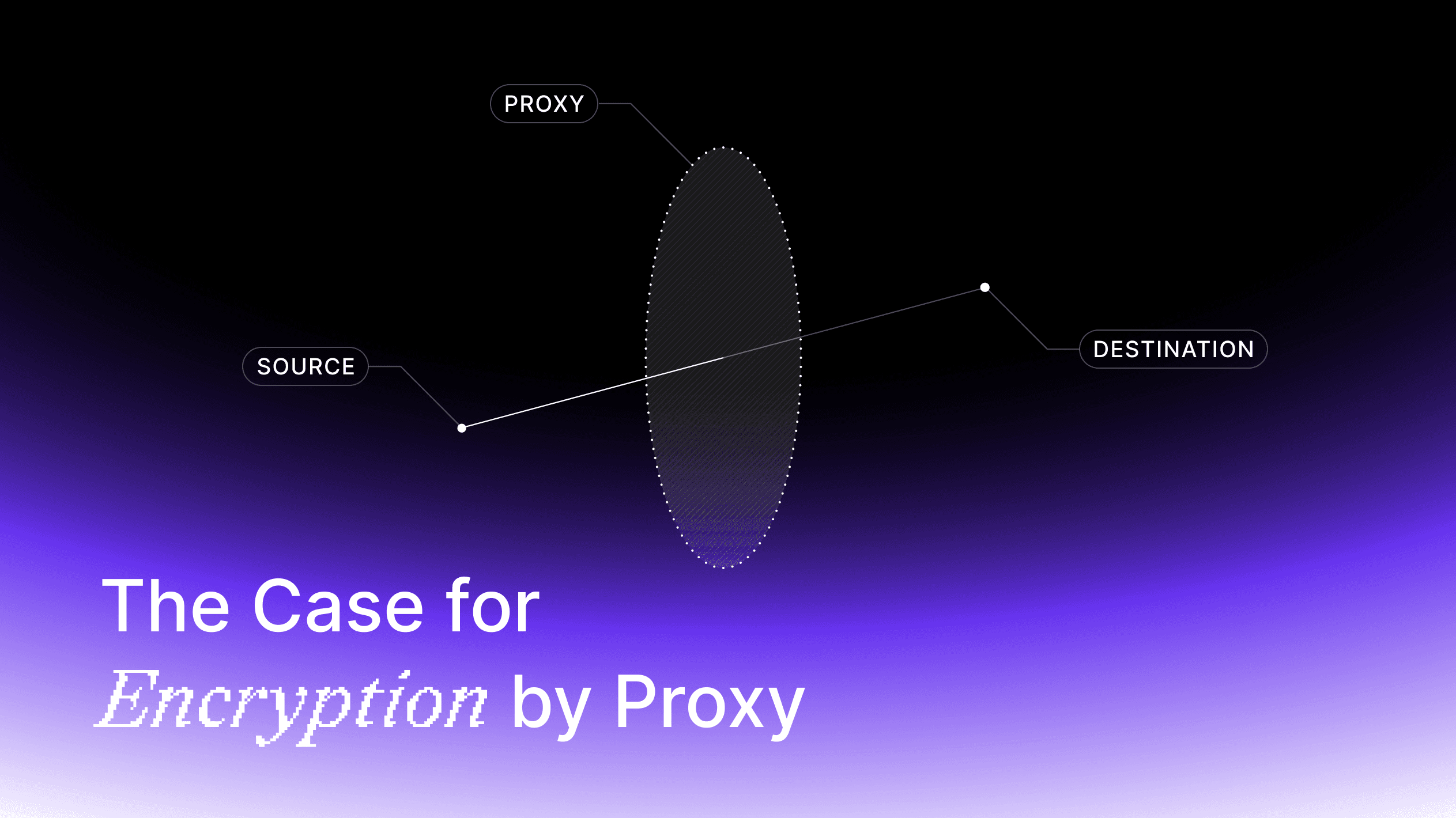
Encryption by proxy - intercept and encrypt data during the network request with a relay server.

In the first episode of Decrypt, get to know your two hosts, Shane Curran and Liz Moy, and learn why they've started his podacst.

HIPAA compliance, Mobile SDKs, FTUX and more! Our team has been hard at work, see what’s new in the Evervault world.
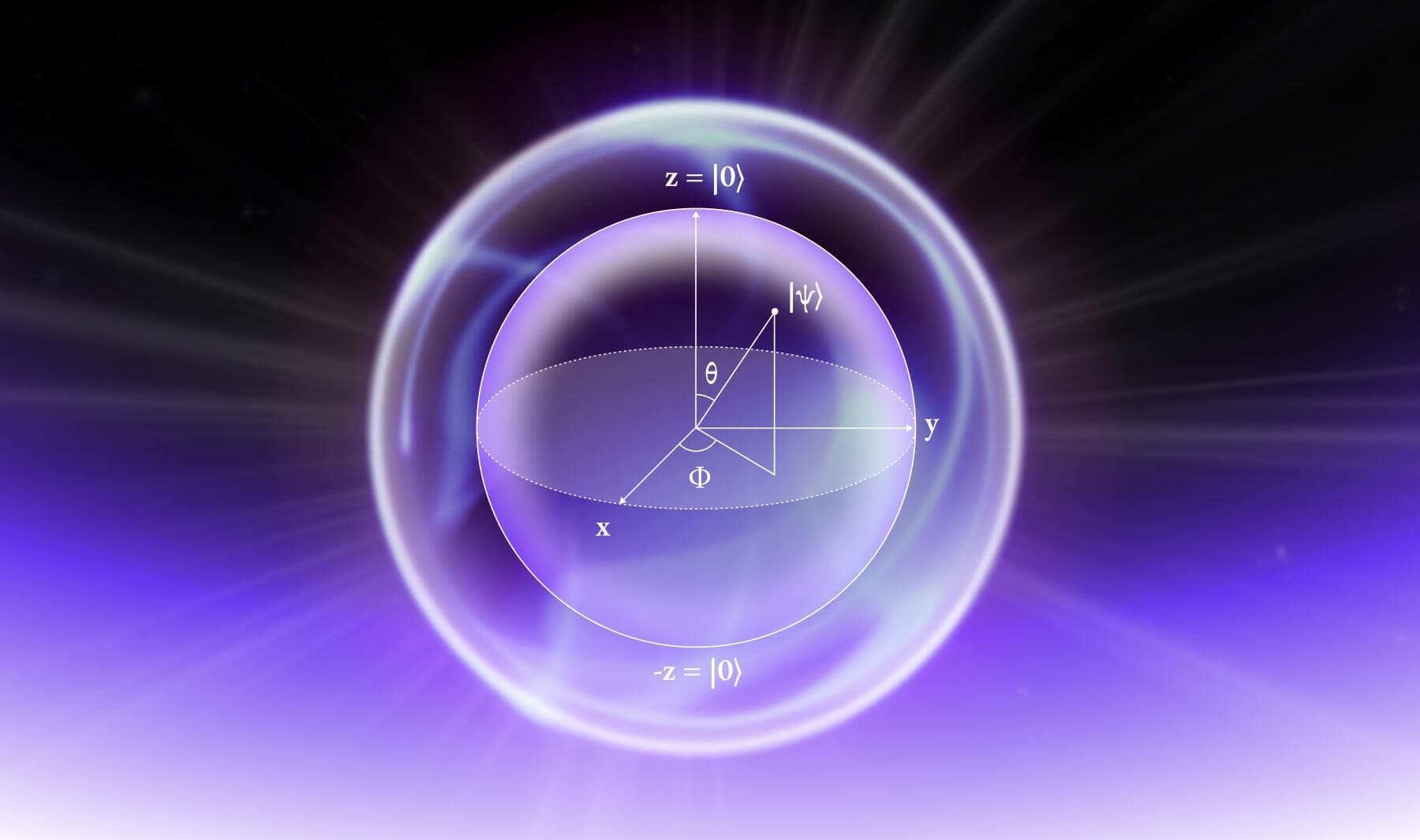
A brief primer on quantum cryptography and quantum cryptanalysis

While federated learning is a big upgrade from centralized learning, it brings its own set of challenges.

Learn how you can secure data that’s actively being changed or updated (in use) and data that you’re keeping in storage, like in a database or CDN (at rest).

Navigating ePHI data security doesn’t have to be a headache. Learn how one startup approached protecting their customer data.

Checkout last month’s feature updates, user experience improvements and content.

An app’s security is often only as strong as its least locked-down integration.

Explaining code attestation, how it enhances data security, and why it needs to be easier.

Safeguarding your Sensitive Data could Save Your Business Millions.

The Crucial Role of Encryption in the 'Shift Left' Paradigm

Bridging the Gap: Enhancing Developer Support and Product Integration in a Remote World

Unlocking E3's Full Potential

Deep dive into our recent product launches, feature updates, and developer demos.

From von Neumann to Secure Enclaves

Overcoming Our Trust Issues

Best Practices to Protect Your API Keys

Building networking from scratch in an enclave environment

Learn the basics of encryption at rest and common mistakes to avoid when implementing encryption.

Providing TLS certificate provisioning and secrets management out of the box

Checkout last month’s product launches, feature updates, and developer demos.

The architecture of a Cage and a step-by-step look at what happens behind the scenes during a Cage deployment.

Demystifying Fully Homomorphic Encryption

How Cage builds preserve the trust model of Enclaves and technical challenges we faced.

Theoretical attacks on SHA-1 have become practical. SHA-1 should be deprecated everywhere.

Ensuring PCI Compliance when collecting payment data with Evervault

Evervault’s take on Secure Enclaves – the importance of accessibility and ease of use when protecting sensitive data.

Checkout last month’s product launches, feature updates, and developer demos.

Understanding how they work and why they matter.

Phone phreaking was a precursor to hacking that paved the way for Apple Inc.

A quick guide to better understanding HIPAA compliance, obligations and requirements to ePHI breach reporting, and the best safeguards for avoiding data breach fallout.

Not sure what is sensitive data and what isn’t? Learn about all the different types of sensitive data and how to protect it when building applications.

Not to mention: excess-3 code, floating decimal arithmetic, self-checking circuits, jump program instructions, taped programs, and 'table-hunting' sub-computers.

Learn about recent changes to the Australia Privacy Act and how you can stay compliant and protect your customer’s data in 2023.
Learn about the DX improvements we’ve made to our website and application and how these changes will make developers’ lives easier.

The Principles of Good Website Design

A seven-step guide to building your encryption architecture, deciding what data to encrypt and how to think about securing it.

Taking your developer docs to the next level.
It’s the most wonderful time of the year.

Everything you need to know about PCI compliance.

Why have production systems fallen behind academic cryptography?
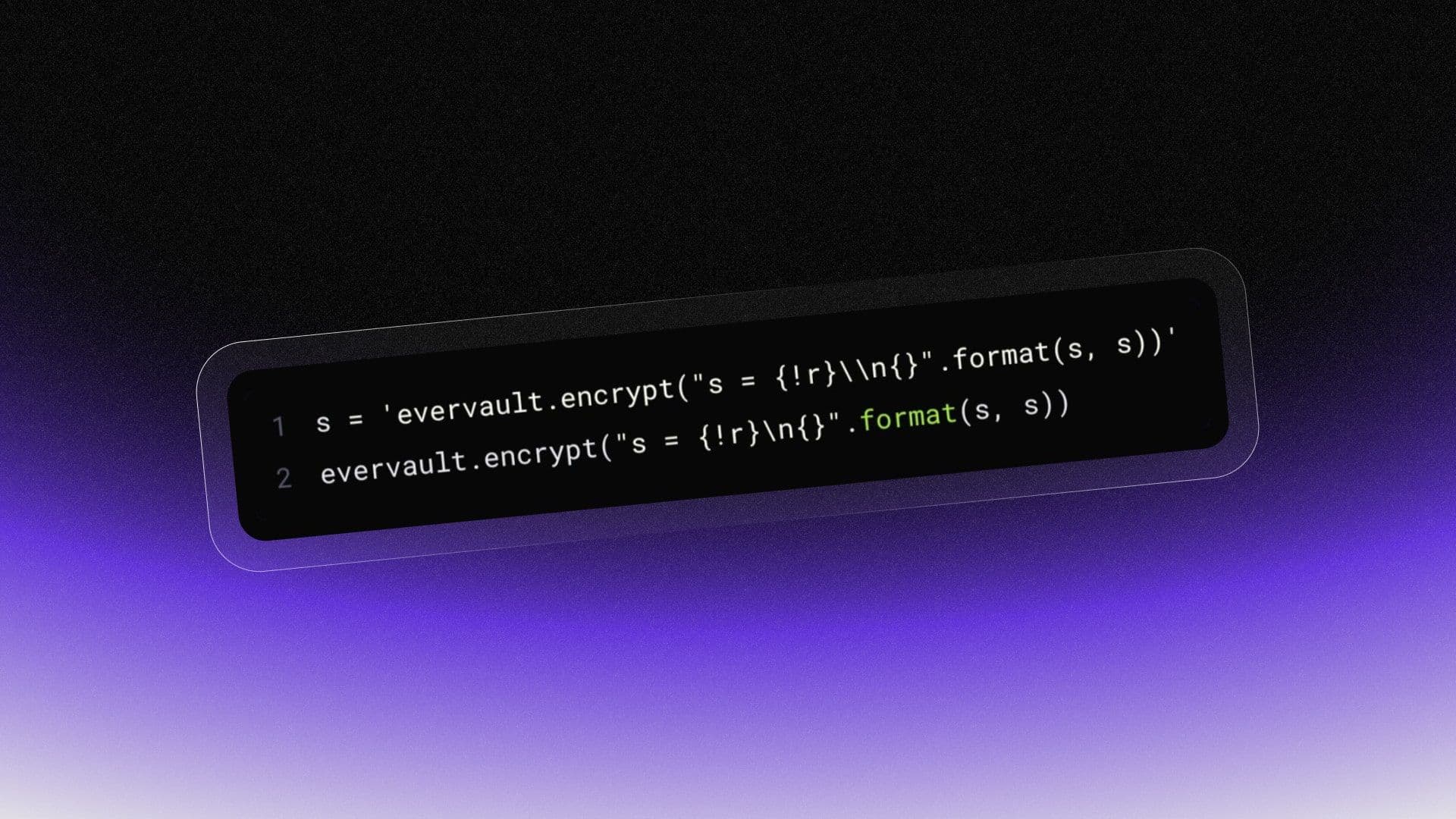
The encryption equivalent of a quine
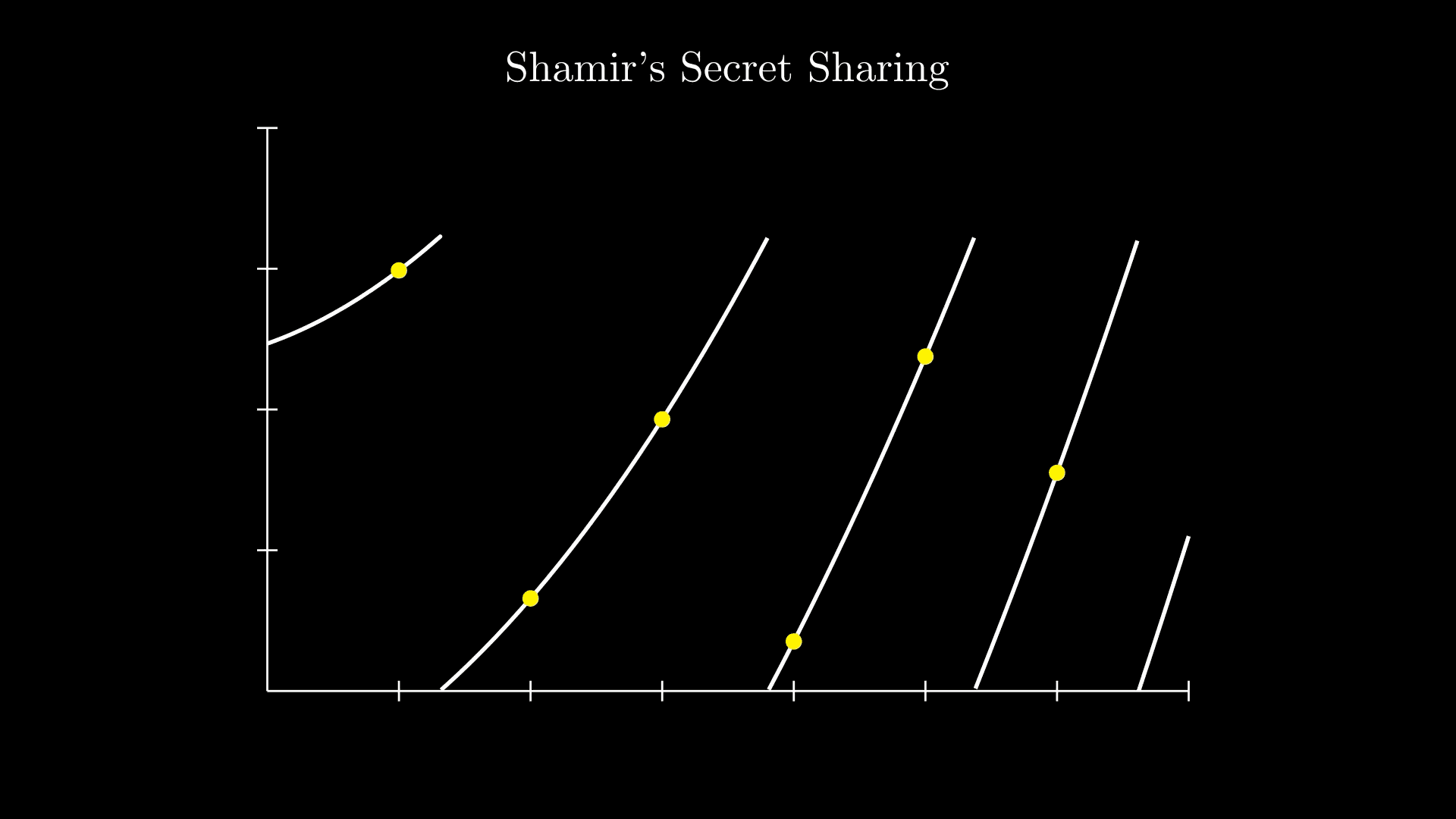
Gain a better understanding of Shamir’s Secret Sharing scheme and its importance with visualization examples from an Evervault engineer.

Encrypting your first string with Evervault

Learn how to use our invisible encryption proxy to automatically intercept and encrypt sensitive fields with field level encryption.

Combating Zero Day Exploits (and data breaches in general) by integrating security from Day Zero.

Using response encryption with Outbound Relay improves the process of querying third parties securely.

Show your users how you protect their sensitive data. Secured by Evervault are hosted pages that confirm a team’s commitment to data security by summarising their encryption architecture.
Evervault is encryption infrastructure for developers. Relay is our latest product to make integrating encryption as easy as possible. This post is about how we built Relay.

Announcing Evervault's 2022 rebrand.

Learn more about how our customers — like Treecard — are using Evervault to reduce their PCI DSS scope to the simplest method of validation.

How Evervault is helping its first PCI DSS customer to protect cardholder data.

We’re excited to announce that Evervault has achieved compliance with HIPAA and SOC 2 Type II.

By building with Evervault, Okra is making sure that Africa’s financial data network is encrypted, safe, and secure.

We’re proud that early adopters have chosen to build their apps and services with Evervault.

How Evervault is helping Vital encrypt health data from wearable devices and at-home test kits.

How Evervault is helping Manna encrypt the data powering their drone delivery network.

Defining our mission at Evervault.

Eight principles for the encrypted web.
Evervault is encryption infrastructure for developers. At the core of this infrastructure is E3, the Evervault Encryption Engine. This post is about how we built E3.

Evervault today announced its $16.4 million Series A round led by Index Ventures, with participation from existing partners Sequoia Capital, Kleiner Perkins, and Frontline.

Evervault today announced its $3.2 million seed round led by Sequoia Capital, with participation from Kleiner Perkins, Frontline, and SV Angel