Encryption in payments: Evervault encryption vs. traditional encryption
Compare traditional encryption vs Evervault for payment security. Explore key management, PCI compliance, and data protection approaches for secure card processing.

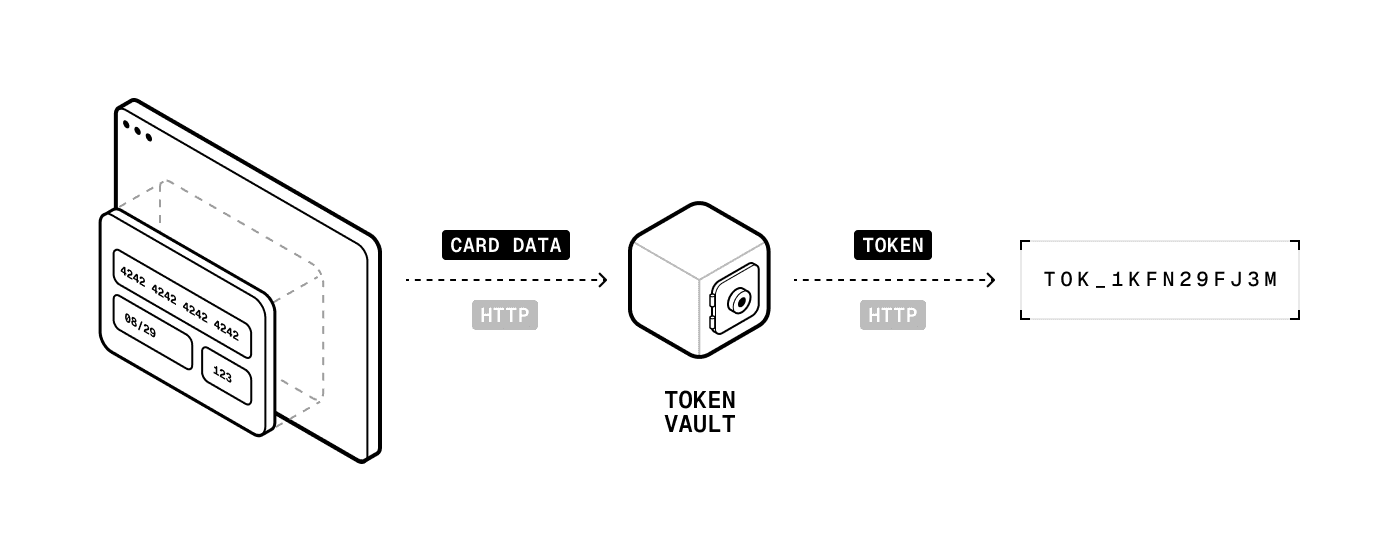
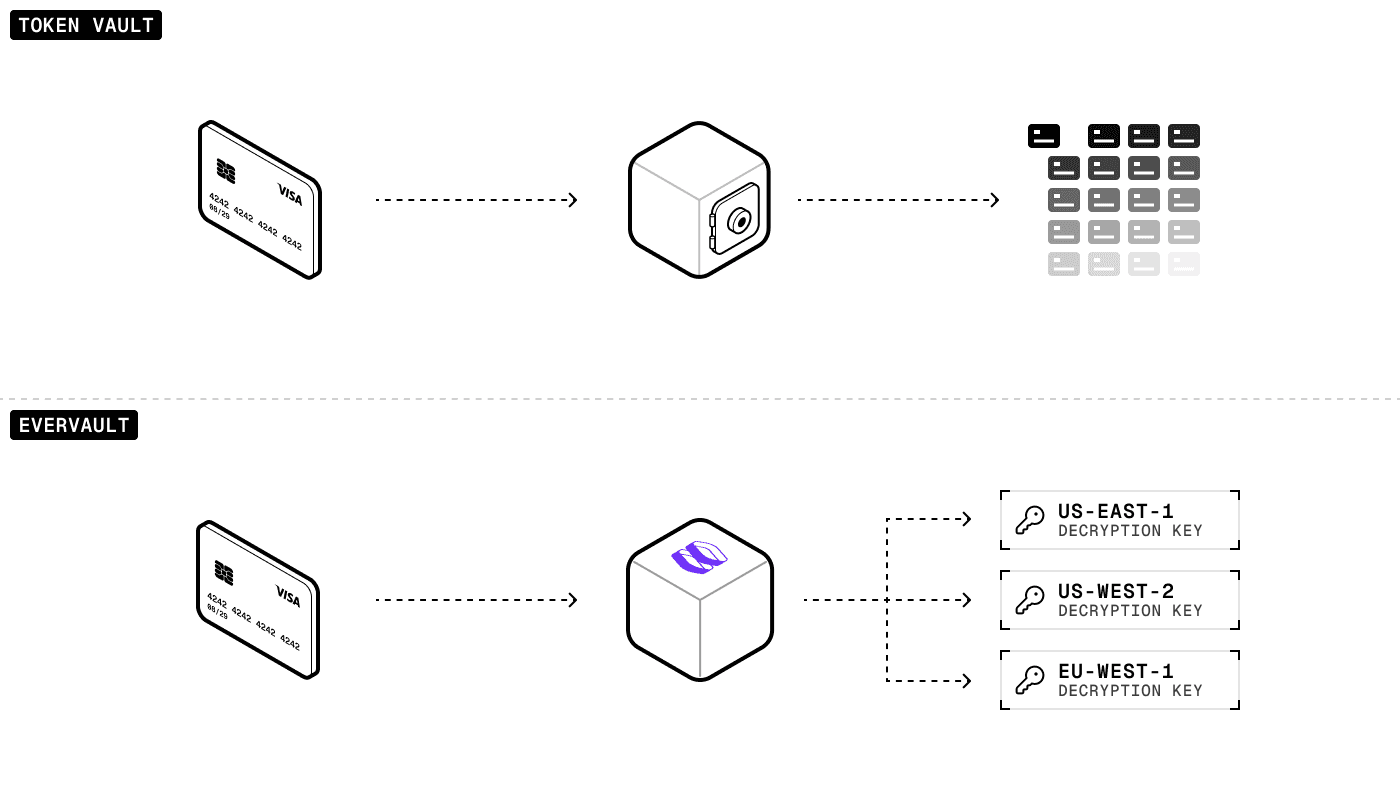
For over a decade, payment tokenization has been the dominant approach for securing card data, helping companies reduce their PCI compliance scope. The concept is straightforward: replace sensitive payment information with tokens that cannot be mathematically reversed to recover the original data (at least in theory). Tokens are stored in a token vault, which is a centralized, secure database with strict access controls.
But here's the problem: tokenization was never designed for the scale, speed, or flexibility that modern payments demand. Token vaults create a single point of failure, add avoidable latency to every transaction, and take ownership of your card data away from you, locking you into the provider.
Every engineer knows the anxiety of depending on infrastructure you can't control. When your tokenization for PCI solution goes down on your biggest volume day, when their database crawls under load, and when you want to migrate but your data is trapped in their systems, you realize that someone else's architectural decisions are limiting your product.
Evervault is different. Instead of storing your card data with us, we split control: you keep encrypted card data in your systems, and we hold the keys to decrypt it. This eliminates the bottlenecks that constrain token vaults, providing better security, performance, and control. All while minimizing PCI DSS scope to the smallest possible control set
Step 1: Card collection The customer enters card details in a secure iframe. The card data is encrypted in transit (using TLS) and sent over the network to the token vault, where it is stored in a central database. A token (basically a database pointer) is returned to you.
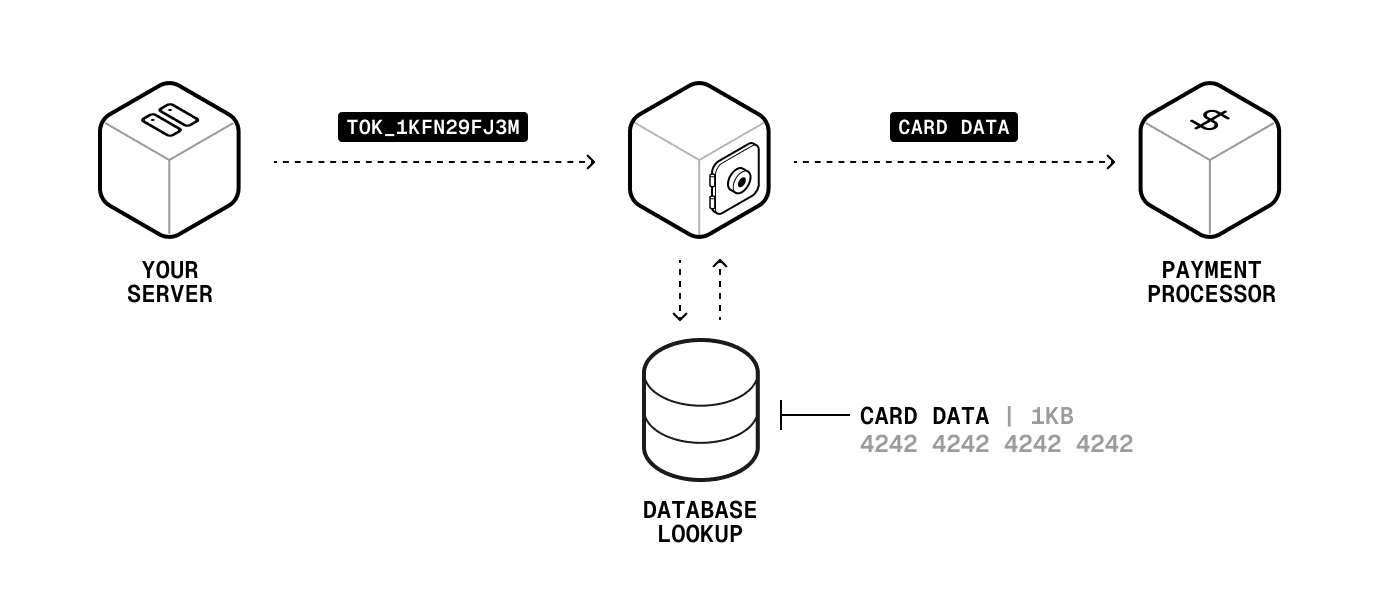
Step 2: Payment processing You send the token. Your provider looks up the card data in their token vault and forwards it to your payment processor.
This approach introduces several architectural constraints that become more problematic at scale:
How It Works:
Step 1: Card collection
Our secure iframe includes a public encryption key specific to your account, which enables card data to be encrypted directly on the user's device in microseconds using hardware acceleration. The encrypted data is transmitted directly to your system, no vault trip is required.
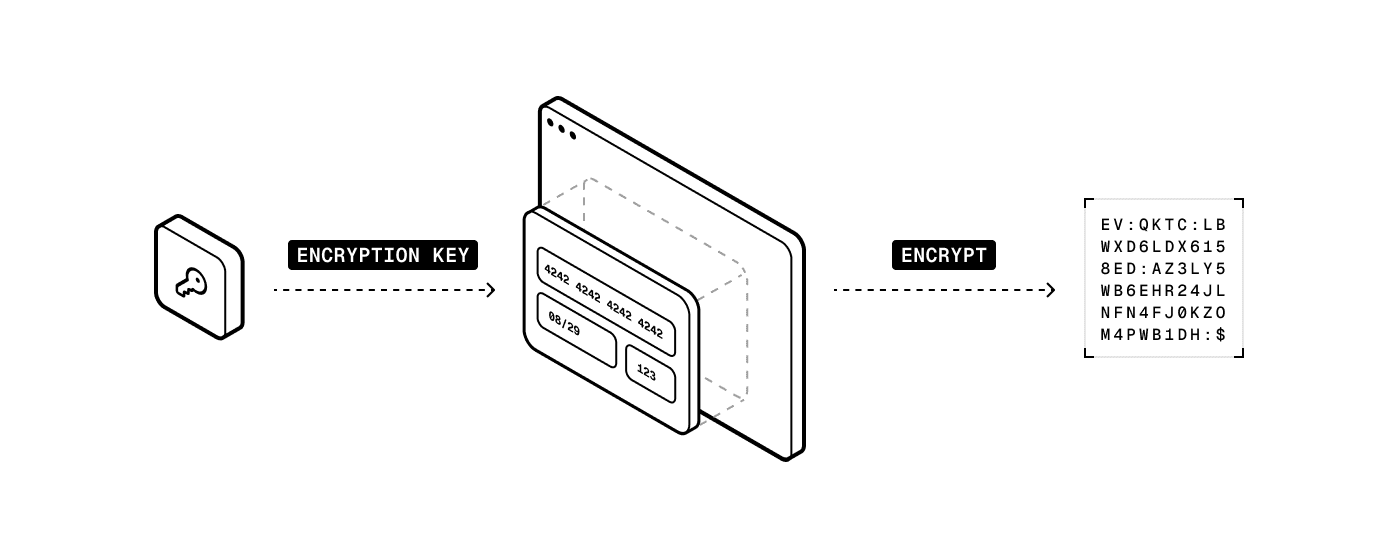
Step 2: Payment processing
You send us encrypted card data. Inside an isolated environment (AWS Nitro Enclave), we grab your 32-byte decryption key from memory, decrypt the data, and forward it to your processor. The decrypted data is permanently deleted within milliseconds.
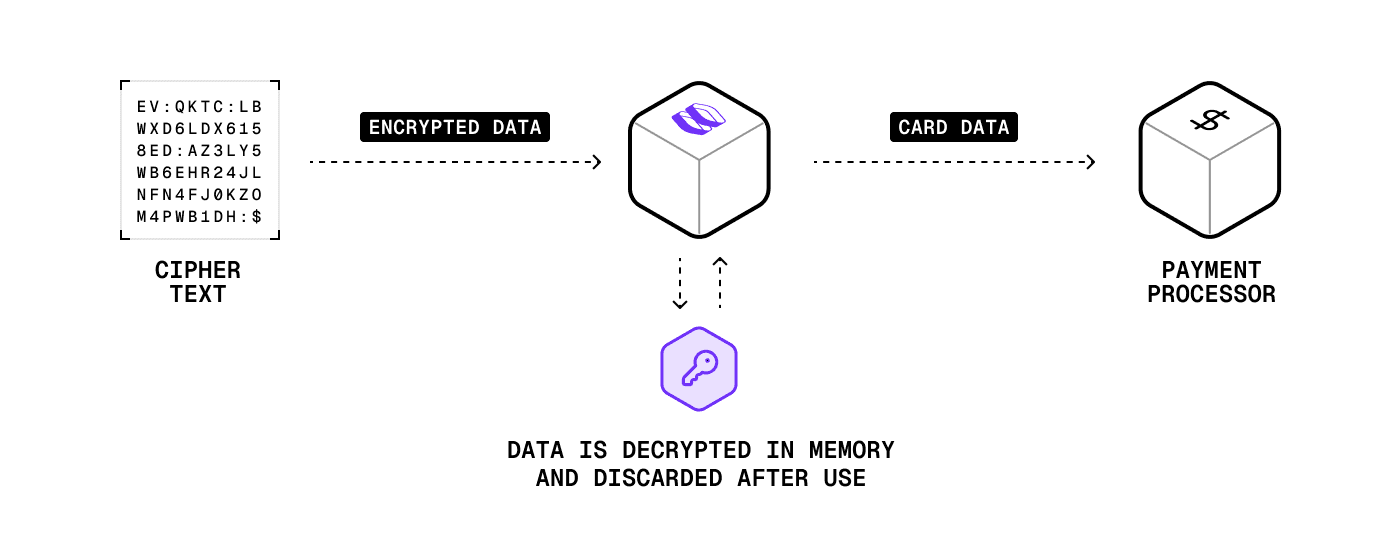
We built this around a simple principle: the most secure data is data that doesn't exist. By storing only tiny encryption keys instead of complete card records, and by processing decryption in isolated environments that auto-delete, we eliminate the persistent targets that token vaults create.
Payment infrastructure needs 99.99%+ uptime. When your tokenization solution fails, your entire payment operation fails. Your customers don't care that "the vault was down", they know your product failed them.
True multi-region: Evervault stores just one 32-byte private encryption key per company we work with. In contrast, a token vault often stores millions of card records per customer, each around 2 KB in size. That’s gigabytes of sensitive data.
Our lightweight footprint is what makes true active-active infrastructure possible. Evervault runs across multiple independent AWS regions by default. If one goes down, traffic instantly shifts to the other, with no lag or failover delay.
Performance under load: Our in-memory key access remains stable during traffic spikes. While token vaults struggle with database optimization under load, we maintain consistent speed regardless of volume.
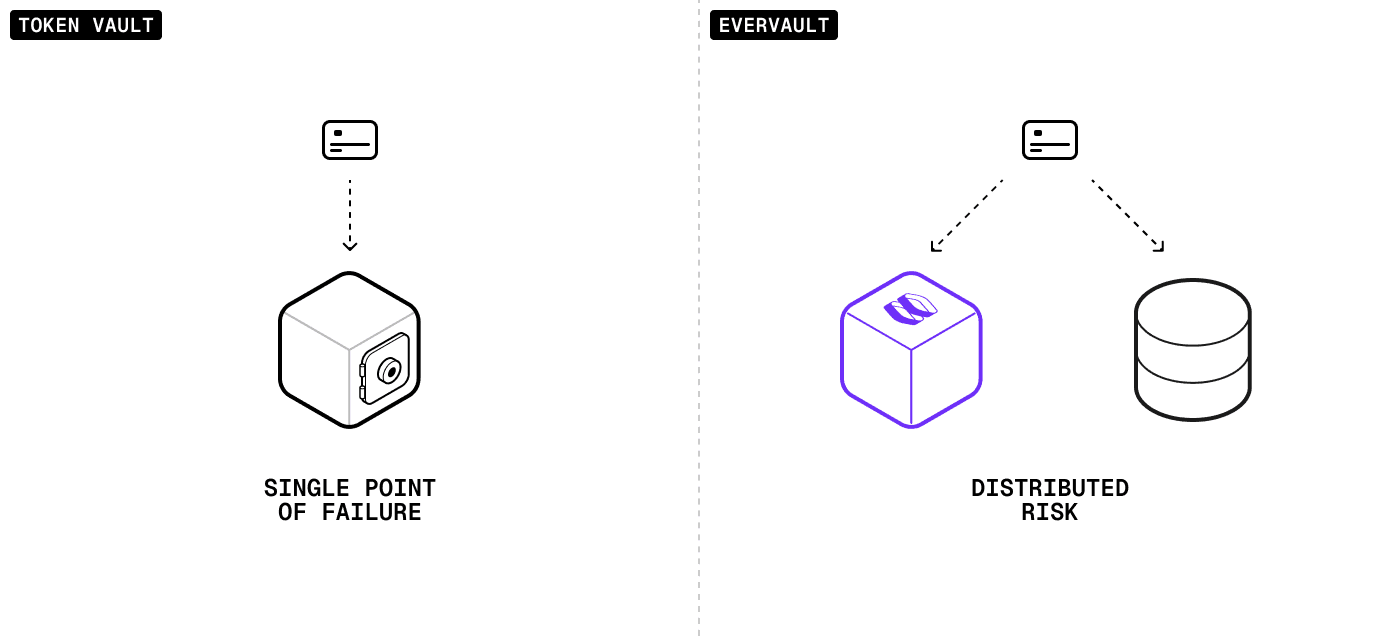
Distributed risk
Token vaults put all your eggs in one basket: a breach exposes everything. With us, attackers must simultaneously compromise two separate, hardened environments (yours and ours) to get raw card data.
Temporary access
Unlike token vaults, where raw card data is stored indefinitely, our system decrypts data only for a fraction of a second before it is permanently deleted, a much smaller attack window. Decryption happens in isolated environments that even we can't penetrate.
With token vaults: You ask for the box, and they go search a giant warehouse by tag, unlock it, then hand it back.
With Evervault: You’ve already got the key, just ask us to unlock the box.
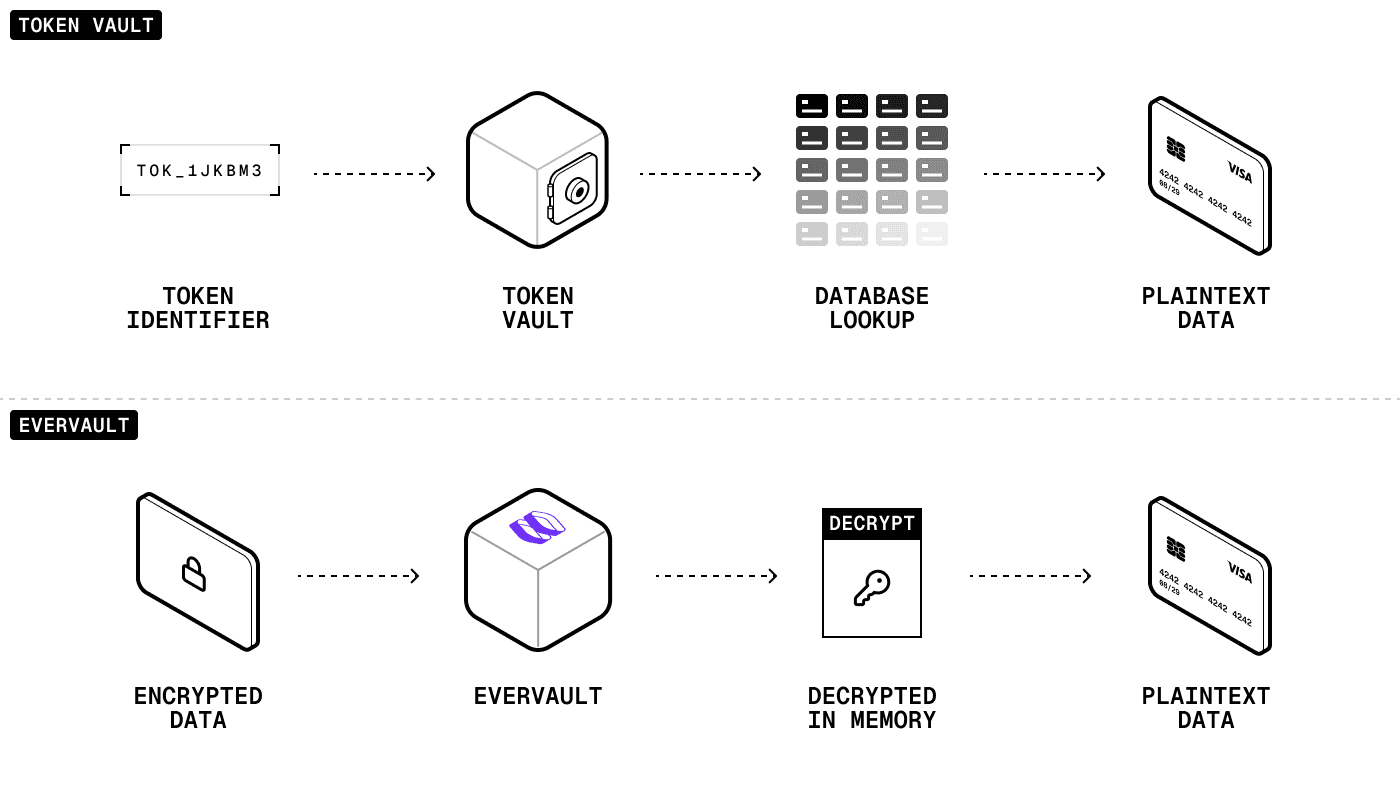
This architectural difference makes Evervault 200-300ms faster:
Never vendor lock-in: With PCI tokenization solutions, migration anxiety is real. Your data exists only in their systems. They control your ability to switch providers.
Escrow-backed exit: We utilize a root key architecture, allowing you to store your master key (or even just shards of your master key) with a third-party escrow provider. With your root key and the encrypted data you already store, you can decrypt everything independently, even if Evervault disappears.
This isn't just a feature, it's a philosophy. We built this for engineers who want control over their architectural decisions.
We only charge when encrypted cards are used, that’s when the actual value is delivered.
| Token Vaults | Evervault | |
|---|---|---|
| Tokenize/encrypt | Y | N |
| Detokenize/decrypt | Y | Y |
| Delete token | Y | N |
Our approach is fundamentally more efficient and, therefore, more economical for you. We encrypt cards on the user's device and store a single, tiny key per customer, regardless of whether they have 10 cards or 10 million. Payment tokenization requires network calls for every card, expensive database lookups, and growing storage costs.
This is especially beneficial for businesses that don't require permanent card storage, such as buy-now-pay-later, virtual cards, and pass-through payments. Why pay three times to tokenize a single-use card that gets discarded immediately? You’ll also need to request your provider to delete the card. With Evervault, you can store the encrypted card and then delete it directly.
Every engineering team faces the same fundamental question: Can you trust the infrastructure you're building on? With payment tokenization solutions, that trust is tested every time traffic spikes, every time you need to scale, every time you want to implement something new.
Evervault provides you with infrastructure that won't fail when it matters, won't hinder you when you need to evolve, and won't become the bottleneck that prevents you from realizing your vision.
"Evervault is built by people who understand and care about the problem, compared to basically everything else we worked with, legacy solutions that have been around for 10 years with crap products that don't really work."
Mike Hudack, CEO of Sling Money
Explore Evervault's encryption-first solution to securing sensitive card data.
Learn more