ASV Scans: What they are, when you need them, and how they work
Learn what ASV scans are, when you need them for PCI compliance, and how Evervault simplifies the process with a modern, user-friendly solution.


Evervault is a Level 1 Service Provider focused on securing organizations in the FinTech and payments space. Our products enable secure cardholder data (CHD) collection and processing while keeping PCI DSS Scope to the absolute minimum, in many cases SAQ A.
You can read more about our PCI DSS services (here).
We work extensively with Prescient Security & Assurance to continuously assess both our SOC 2 Type 2 and PCI DSS compliance.
As a data security company, Evervault is keenly aware of the importance of information security, industry, and regulatory compliance. We knew that to succeed as a security company, we needed to build our platform and products with best-in-class and state-of-the-art security at the forefront of everything we do. We also knew that security alone is insufficient to compete in a crowded sector. Compliance with standards like PCI DSS Level 1, external assessment to SOC 2 Type 2, and strict alignment with privacy laws were all table stakes.
We knew we needed a partner familiar with the payment security problems we solve and how our novel methods for solving these problems translate to standards, regulations, reduced risk, and value to our customers.
We chose Prescient Security as our partner to evaluate our systems, policies, and processes. We took a joint approach to merging a continuous audit process for SOC 2 with our annual PCI DSS v4 Level 1 Service Provider assessment. While PCI DSS v4 is not mandatory until March 2024, we chose to be one of the first companies to achieve PCI DSS V4 compliance. Evervault was the first of Prescient’s customers to do so.
The partnership has proven invaluable in its flexibility. It was brought to life in the determination of our PCI DSS Customized Validation, which we undertook in July 2023. The control in question was 8.3.4, which aims to prevent successful brute force attacks on in scope systems.
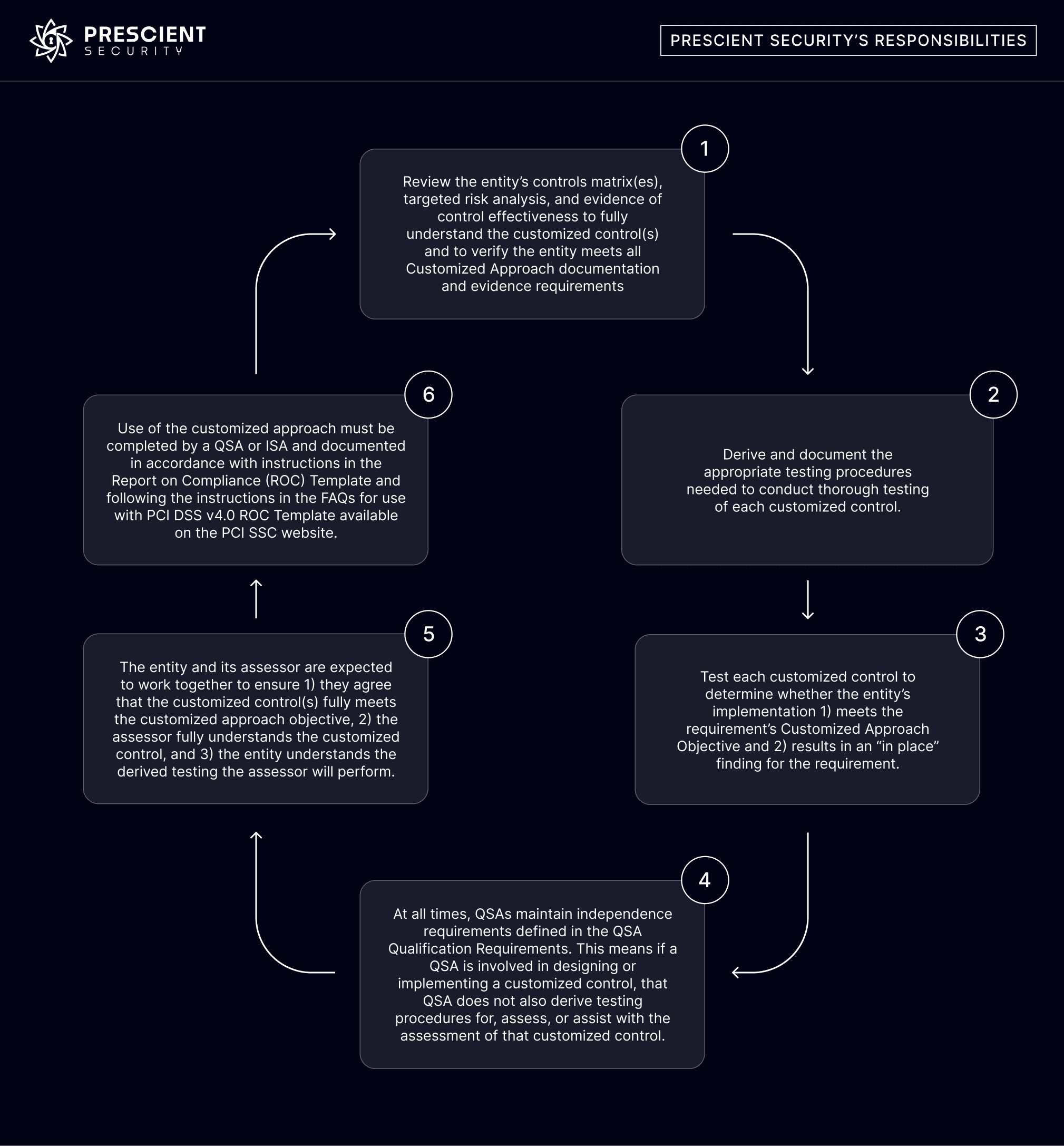
The PCI council is extremely prescriptive about how Customized Validation must be used, with large amounts of effort involved in year one by both the QSA and the auditee. The requirements are summarized in the diagrams below, and an examination of our documentation is also presented from Risk Assessment to the RoC.
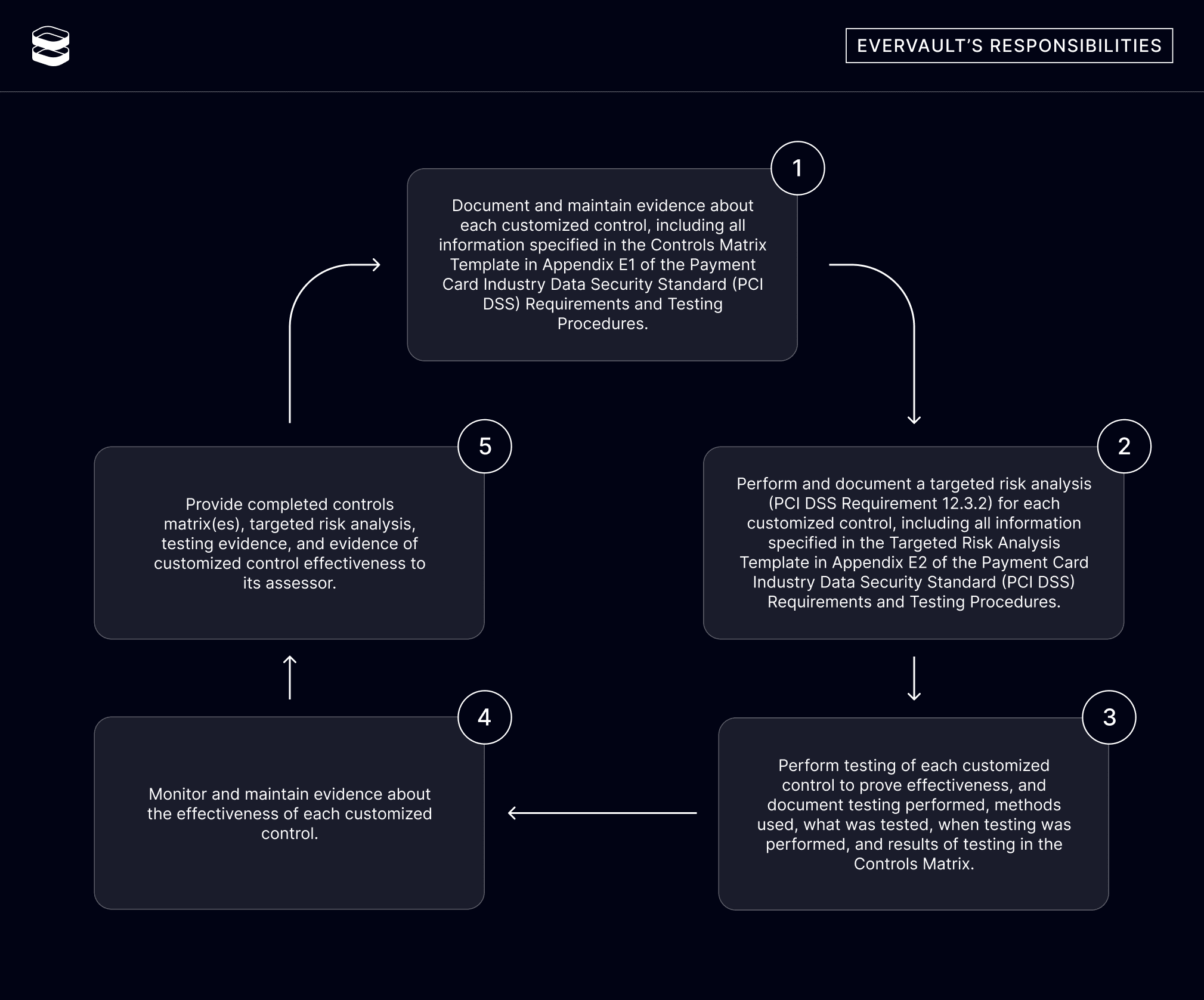
The first step for Evervault was to execute the Risk Assessment for a common issue that will be encountered by everyone using a Cloud Service Provider.
Evervault Risk Analysis: Account-Lockout & Brute Force Mitigation
This analysis describes an approach for mitigating the need for account lockout to prevent brute force attacks on our primary authentication system by utilizing hardware-based YubiKeys in the context of Payment Card Industry Data Security Standard (PCI DSS) v4. The strategy leverages the additional layer of security provided by the YubiKey U2F / Fido2 as an authentication mechanism, thereby reducing the risk of successful brute force attacks and ensuring continued compliance with PCI DSS v4 requirements.
PCI DSS v4 specifies requirements for securing cardholder data, with a focus on security technologies and a risk-based / Customized Validation approach. This includes requirements for securing systems against unauthorized access, which traditionally involves account lockouts after several failed login attempts to prevent brute force attacks (8.3.4).
However, with the introduction of hardware-based YubiKeys with Fido 2 and U2F as an additional authentication factor and console access restricted via mutually authenticated VPN, there's potential for an alternative approach that can mitigate the risk of successful brute force attacks without the necessity for account lockouts and offering more reliable and user-friendly access management.
YubiKeys provide a high level of security by employing two-factor authentication (2FA) with Origin binding (verifying the device is authenticated as well as the hardware and user credentials to a specific website), thus minimizing the risk of unauthorized access even in cases where a password or authentication token is compromised. This compensates for the need for account lockouts due to the increased difficulty and reduced likelihood of successful brute-force attacks.
The approach involves replacing the account lockout feature with a multi-factor authentication process using YubiKeys and MTLS VPN. The process is as follows:
This approach provides significant risk mitigation:
The use of YubiKeys for two-factor HW keys and the restricted network console access meets the intent of the PCI DSS v4 requirements for securing systems against unauthorized access. This approach mitigates the risk of brute force attacks, thus compensating for the need for account lockouts.
By implementing YubiKeys as a multi-factor authentication measure, we can ensure robust security against unauthorized access and brute force attacks while adhering to the principles and intent of the PCI DSS v4.
As the Qualified Security Assessor for the Evervault PCI DSS v4.0 assessment, our responsibilities associated with the use of the customized approach elected by Evervault included the following:
The Prescient Security QSA performing the Evervault assessment completed all these steps and documented the results within the PCI DSS v4.0 r1 ROC Template for Evervault, with the result of an “in place” finding for the requirement.
In addition to meeting the technical requirements of the PCI DSS, we found that the Evervault use of the customized control addressed a common weakness of the native authentication capabilities of the major cloud infrastructure technology service providers regarding the automation of account lockout in the event of a suspected brute force attack. The additional origin binding feature of the YubiKey implementation effectively blocks login attempts from unspecified domains, which we believe is one of the primary risks that is addressed by the standard approach to complying with requirement 8.3.4. The YubiKey also satisfied the requirement for a second authentication factor in addition to the password associated with the user account.
We believe that the Evervault implementation of the YubiKey with origin binding is an example of a creative approach to addressing administrative account access security controls required by the PCI DSS using a Customized Control. In addition, it eliminated the need for a common compensating control requirement associated with native IaaS password security policy limitations. We all understand the password management tends to be a common point of weakness in the overall access control security architecture, and we believe the additional requirement of using a hardware token to authenticate all access to the most sensitive areas of the cardholder data environment to be an excellent additional layer of control.
With PCI DSS V4 and particularly with Customized Validations, there is a lot of work to do in year one; however, once complete and developed in a way that is acceptable to the QSA and is defensible and secure, the up-keep of the control in this instance is relatively straight forward and can be improved continuously to reduce manual effort. For example, alerts could be set up to notify a user of being set up without HW MFA or to notify of the removal of an HW key with automatic suspension of an account.
Evervault is a PCI DSS v4 Certified Level 1 Service Provider. We provide an end-to-end PCI DSS solution to allow customers to derisk successful card breach, descope their environments from PCI DSS and achieve compliance, simply. With PCI DSS v4 imminent (March 2024), many organizations are re-evaluating their approach to PCI Compliance, opting to use the opportunity to descope instead of piling effort into the required uplift to achieve V4.
If you need help with PCI DSS or would like a template of this Customized Validation to use for your own audit, Contact us, sales@evervault.com
If you do plan to plough through the uplift to PCI V4, ensure you contact Prescient Security to help you with gap analysis and PCI Support to ensure a successful outcome - saleshelp@prescientsecurity.com
Book an initial consultation with the Evervault team, and we'll work with you to evaluate your payment security options.
Learn more about Evervault PCI