

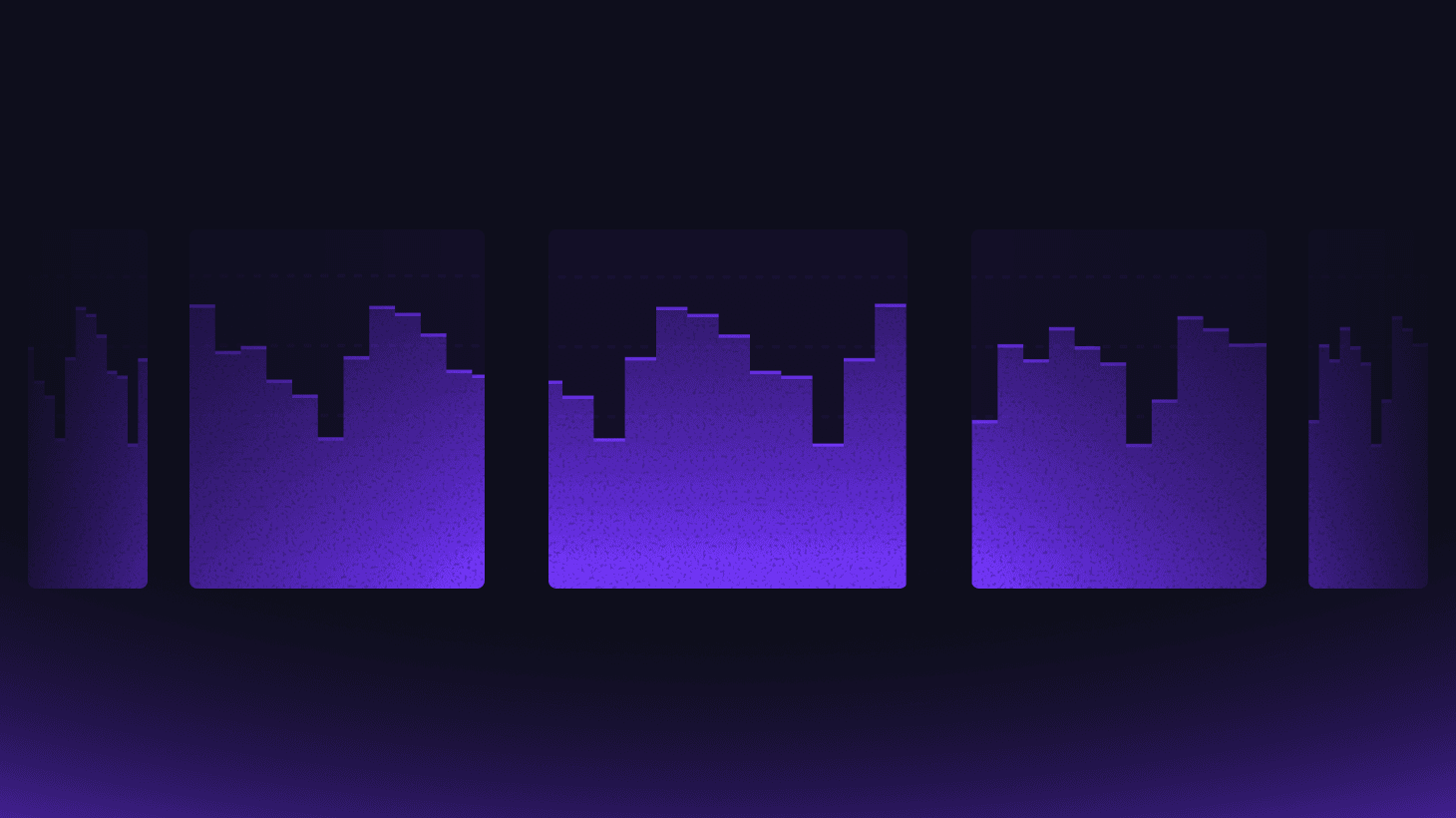
New metrics are now available in the Evervault dashboard. Personalize your metrics view with the features most important to you. You can choose metrics for decrypts, encrypts, inspects, 3DS sessions, network tokens, and BIN lookups. All metrics can be filtered for the past 24 hours, 7 days, or 30 days.
Relays, functions, and enclave metrics have also received an update. You can now see the total number of requests, failures, and latency in a given timeframe. Hover over each chart to see the breakdown of requests per instance, and click to view the relevant logs.
Quick links will now appear for recently visited pages, such as Relays, Functions, or Page Protection pages. Monthly billing details are also available for a quick glance at your team’s usage.
insights category in logs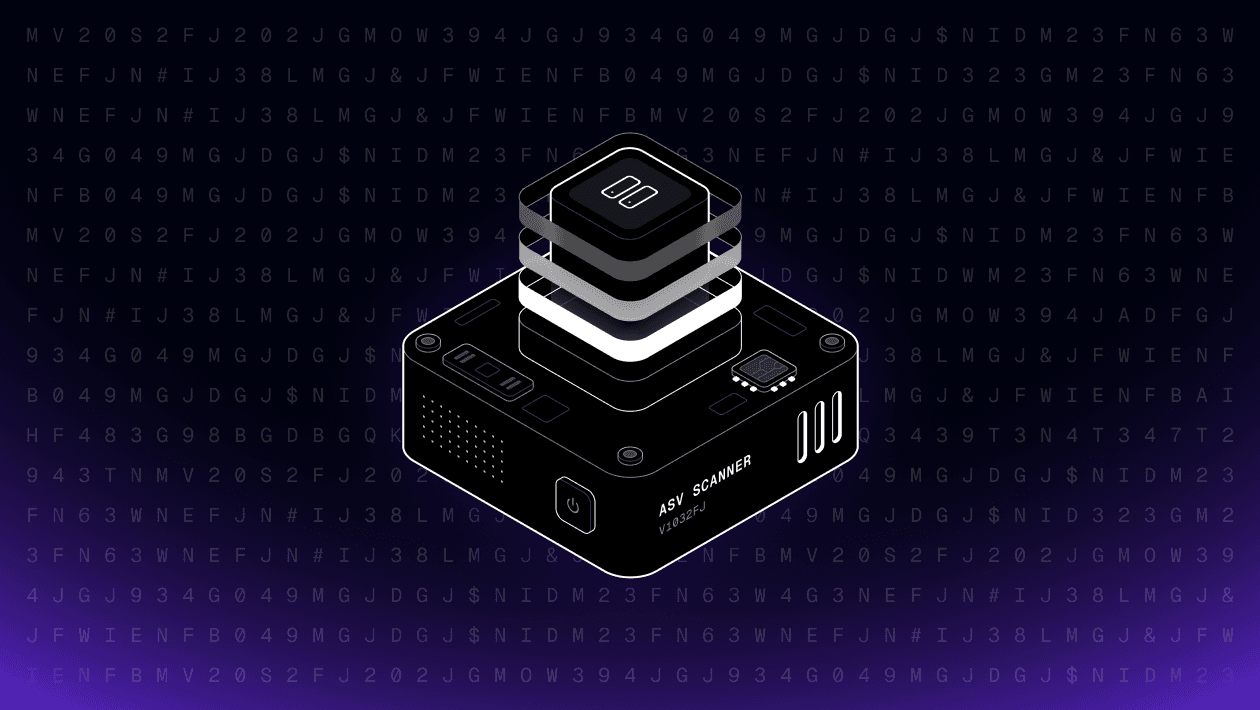
You can now run ASV (Approved Scanning Vendor) scans with Evervault. These scans are part of the PCI Data Security Standard (specifically requirement 11.3.2). If you’re in scope for that requirement, you need to submit a passing ASV scan at least every three months or 90 days. Evervault recommends completing your scan well ahead of the deadline. Many customers submit monthly to enhance security and allow for early identification and resolution of any issues. Contact your account manager to get started, or check out our docs for more information.
ASV scanning is part of our continuing effort to build out the compliance tooling side of our platform. Legacy tools in this space are often clunky and inefficient, and because you’re likely using Evervault’s other products already, it made sense to add ASV scanning. While not a complete list, below are some of the key benefits to our solution.

You can now accept Apple Pay and Google Pay with Evervault in native apps with our Swift & Android SDKs.
You can now create and manage merchants from the new Payments view in the Evervault Dashboard. From here you can:
We’ve launched a new hub for our monthly webinars allowing you to easily go back and watch any webinars you might have missed.
validation option to allow developers to add custom validation logic. For now this only supports adding regex validation to the card holder name, however, we plan to expand this to other validation types and inputs.onPaymentMethodChange hook to allow developers to respond to users selected different payment methods inside of the payment sheet.
Jump anywhere in the dashboard with the new command palette. Triggered with ⌘ + K (Ctrl + K on Windows). The palette surfaces shortcuts to pages, actions, and recent items, so you no longer dig through menus. Fewer clicks mean you stay in flow and find what you need faster.
Set up subscription billing in a single tap. Our Apple Pay component now supports recurring payments. Customers approve an ongoing charge in the familiar Apple Pay sheet, making renewals effortless.
Pipe traffic straight from your VPC into Enclave without touching the public internet. Compliance teams gain peace of mind and sensitive data stays on your network. Reach out to support if you want to enable Private Link on your Enclave.
repareTransaction option for Apple Pay which allows merchants to adjust pricing just before the sheet appears.onShippingAddressChange hook in Apple Pay to allow merchants to recalculate the price when the address updates.
Today, Evervault is launching Page Protection, a browser script management product that helps payment companies and merchants secure their payment pages against script attacks and comply with the latest PCI DSS 4.0 compliance requirements (6.4.3 and 11.6.1). Page Protection routes external scripts through Evervault’s secure CDN, continuously monitoring them so you instantly spot anything suspicious.
You can now collect billing address information with Google Pay using the new billingAddress option.
evervault.ui.googlePay(transaction, {
billingAddress: true
})
Our new Card Art API is an extension for Network Tokens that lets you fetch the official artwork for a card.
availability method to our Apple Pay component to allow you to check for Apple Pay support on the device before rendering the Apple Pay button. Learn more
We have released a new major version of our React Native SDK. This is a complete rewrite of the SDK which is now compatible with the new React Native architecture. Our React Native SDK enables your team to safely collect payment details and reduce fraud with 3D Secure.

We've released a new @evervault/js package to allow our browser SDK to be imported as a CommonJS module or ES module. The package provides typescript types for use inside of typescript codebases.