Evaluating network tokens: Webinar Q&A
Network tokenization promises better authorization rates, reduced fraud, and enhanced security, but implementing it comes with real questions.

Even today, payment fraud continues to pose a significant challenge for online merchants, banks, and consumers worldwide. Part of it is volume; there are more e-commerce transactions than ever before. Another part is the growing sophistication of adversaries—fraudsters are developing new methods for exploiting vulnerabilities in payment systems.
One of the tools in VISA’s arsenal to combat fraud is EMV 3D-Secure (or 3DS). EMV 3D-Secure is an evolution of the original 3D-Secure protocol, which provided extra steps to verify a payers identity. EMV 3D-Secure leverages advanced authentication methods and risk-based analysis while maintaining a streamlined user experience.
In short, EMV 3D-Secure balances two competing needs: (a) a mitigation of fraud threats and (b) a maintenance of high success rates. Without strong enough security, too many fraudulent payments will pass; however, with too onerous tactics, too many consumers will abandon payments in frustration. For merchants, it has a bonus perk—in the event of a chargeback, liability shifts from the merchant to the card issuer.
Notably, in Europe, EMV 3D-Secure is mandatory under the Strong Customer Authentication (SCA) component of the Revised Payment Service Directive (PSD2). There are exemptions—such as for merchants that process transactions under 30 euros or merchants that can demonstrate fraud rates are exceptionally low for their customer base. However, generally speaking, EMV 3DS is required, forcing most companies with a European base to implement it.
By enabling real-time information sharing between merchants, payment networks, and card issuers, the EMV 3D-Secure helps prevent fraud and minimize chargeback costs while minimizing unnecessary payment disruptions. Let’s dive into how.
The journey of 3D-Secure began in 1999 when Visa developed the original protocol, commonly known as “Verified by Visa.” While innovative for its time, the first version faced several challenges, particularly regarding user experience. The mandatory authentication pop-up windows often confused customers and led to cart abandonment, affecting merchants’ conversion rates.
Recognizing these limitations, the payment industry collaborated with EMVCo—a consortium founded by VISA, Mastercard, Discover, AMEX, JC, and China UnionPay—to develop EMV 3D-Secure. This new version introduced significant improvements:
EMVCo served as a third-party entity that backed standardization across the industry, leading to broader adoption and interoperability between different payment systems and card networks.
The EMV 3DS protocol operates through three primary components working in concert:
Directory Servers (or DS) are operated by card networks. They route authentication requests and verify merchant and issuer participation.
Access Control Servers (or ACS) are managed by card issuers. They perform cardholder authentication and apply any risk-based assessment rules.
3DS Servers integrate with merchant systems and initiate the authentication requests, processing the returned responses.
These are just the components of the EMV 3DS protocol. They can be leveraged for two possible paths.
In a frictionless flow, merchants process a low-risk payment without any additional challenge. Step-by-step, this amounts to:
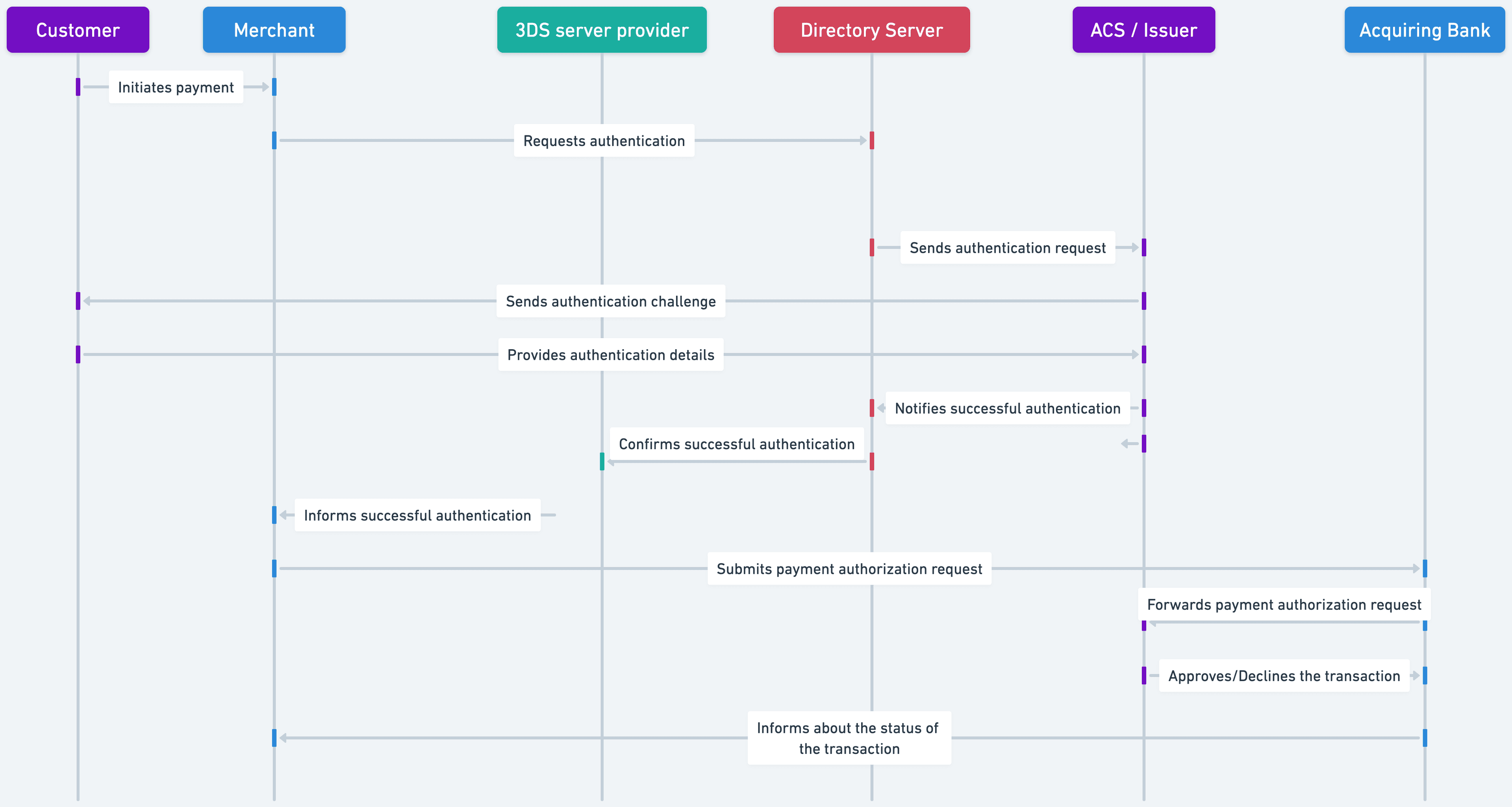
If the risk assessment prompts the need for verification, a challenge flow is invoked, where additional verification is required. Step-by-step, this amounts to:
See below for an overview of a succussful 3DS challenge flow.
By leveraging a third-party service or VISA’s SDKs, merchants evaluate risk by analyzing (i) device information, (ii) transaction history, (iii) location data, (iv) shopping behavior patterns, (v) payment amounts and currency types, (vi) and a merchant’s overall risk indicators.
One of the cornerstone principles of EMV 3D-Secure is to support multiple verification methods so that the right methods could be invoked for the right customer and the right merchant.
Verification methods available to challenge flows include:
A temporary code is sent via SMS or email that the cardholder must enter to verify their identity during the transaction.
Unique physical characteristics like fingerprint, facial recognition, or voice recognition are used to verify the cardholder’s identity through their device.
An authentication request is sent directly to the cardholder’s banking application, where they can securely approve the transaction within their trusted bank environment.
Verification occurs through security questions and personal information that only the legitimate cardholder should know.
Verification occurs through a separate communication channel—typically through a bank’s mobile app or other secure channel—effectively separating the authentication from the main browser/payment flow.
This specialized form of authentication allows for a delay between the initial request and completion, enabling verification on a different device. This method is particularly useful for mail order and telephone order transactions.
Additional improvements to the EMV 3DS protocol are on the horizon. These include enhanced biometric integrations, better AI-powered risk engines, support for more niche devices, Internet of Things (IoT) payment support, and integrations with any new authentication methods.
In general, we expect to have more passwordless authentication, biometrics, and AI integrations in the space.
EMV 3D-Secure represents a crucial advancement in online payment security, balancing robust fraud prevention with optimal user experience. As e-commerce continues to grow, implementing EMV 3DS becomes increasingly important for merchants wanting to protect their business and customers.
For merchants considering implementation, the initial investment in time and resources is outweighed by the long-term benefits of reduced fraud, improved customer confidence, and regulatory compliance. Working with experienced payment partners and following industry best practices ensures successful deployment and ongoing optimization of the protocol.