ASV Scans: What they are, when you need them, and how they work
Learn what ASV scans are, when you need them for PCI compliance, and how Evervault simplifies the process with a modern, user-friendly solution.


In this installment of our ongoing threat model series, we delve into the realm of external attacker threats, drawing upon the valuable insights of the Mitre Att&ck framework.
If you’re just joining us, we strongly recommend you read the first part of the series which introduces the concept of threat modeling and defines the relevant key terms and tech stack for the series.
If you don’t heed our recommendation, the main thing you need to know from Part 1 is that we are considering an internet-facing application handling sensitive health and credit card information. The application is a typical three-layer architecture with web, application, and data storage layers and is hosted in a public cloud across data centers in the US and EU.
Given the excellent work by Mitre in defining attacks, we won’t reinvent the wheel.
The figure below illustrates the Mitre Att&ck model, configured to show the many variations and paths an attacker may take while compromising a cloud-based Software as a Service (SaaS) platform.
For most commercial SaaS platforms, attackers pursue one overarching objective: monetization. This typically materializes in two distinct ways:
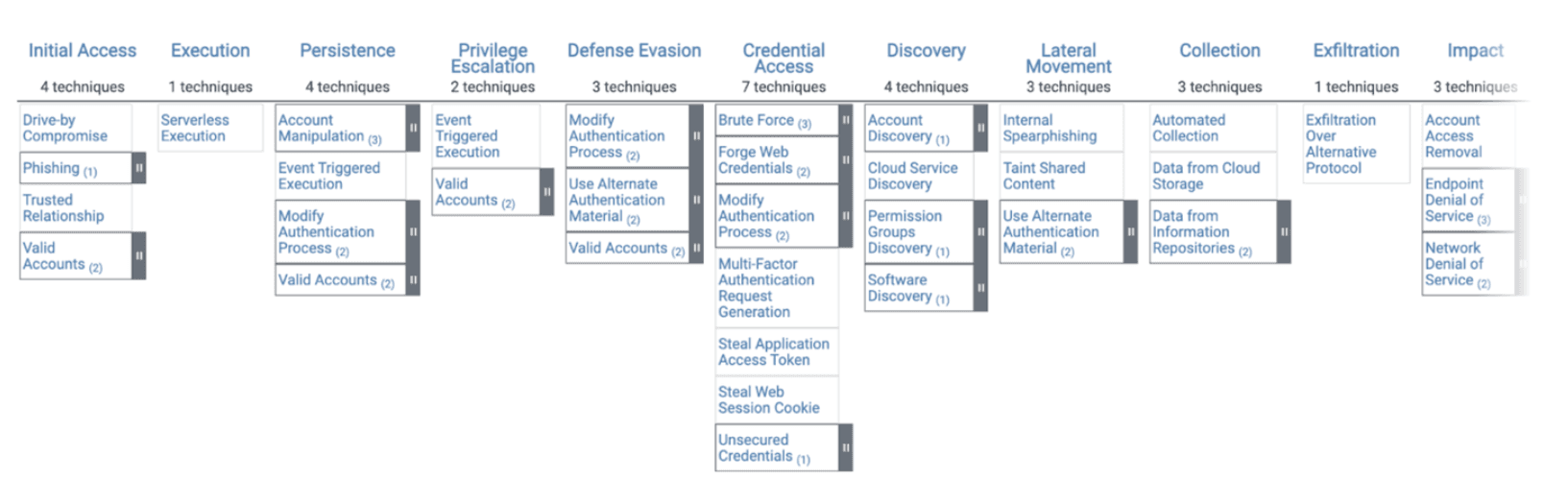
In addition to the above attack vectors, a couple of other initial attack methods warrant consideration, notably the exploitation of vulnerable internet-facing components and cloud misconfigurations leading to overly permissive access. We will revisit this flow later.
Regrettably, the level of sophistication required for attackers to compromise a web-based SaaS product remains relatively modest, especially when the target organization lacks fundamental defenses or does not monitor for changes in its cloud security posture. With tools like Evilginx being widely available and easily deployable, successful attacks, even against Multi-Factor Authentication-enabled targets, are achievable by those with foundational technical ability.
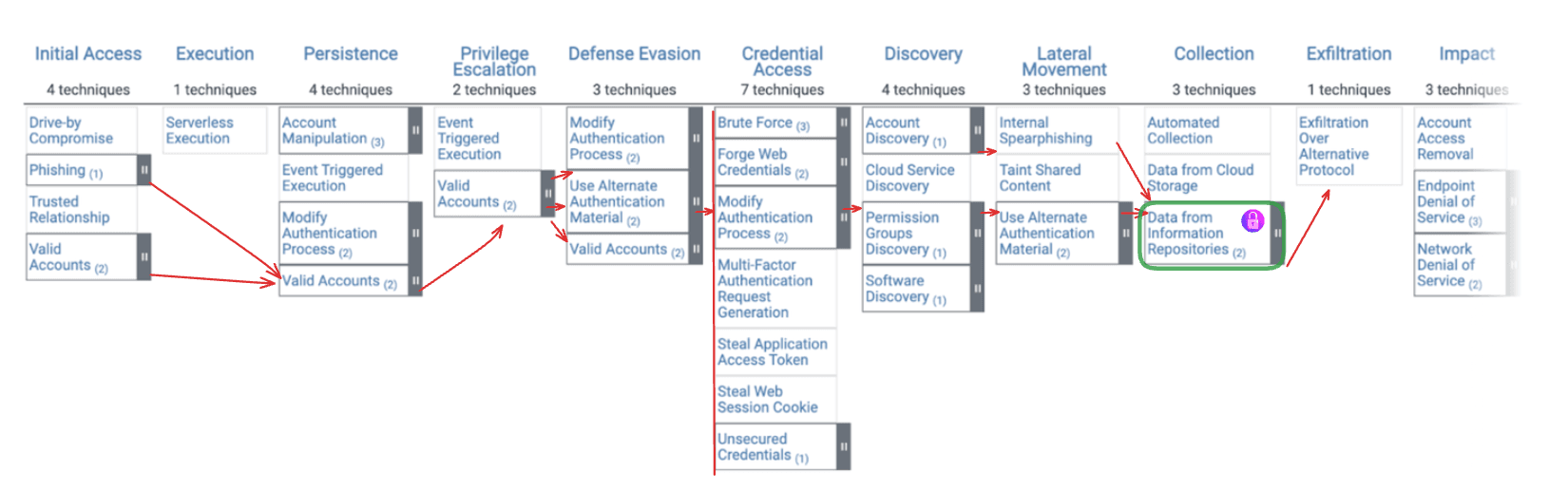
While many threats exist, we will stick to the Data Theft scenario for this review, as mentioned below.
While it is clear there are many attack vectors to consider and several layers of controls that should be layered on top, we will just consider the scenario where an attacker has phished cloud environment administrative credentials, as this is still all too common.
This attack flow unfolds as depicted, with red arrows tracing the various routes leading to the eventual access and exfiltration of valuable data.
Mitigations can be visualized and mapped onto the diagram, this time depicted in green. Many preventative controls can be employed to mitigate risk. However, once an attacker is “in” remaining mitigations revolve around impeding lateral movement and identifying signs of anomalous behavior, thereby minimizing the breach's impact. The one exception here is encryption, which, when well implemented with robust key management, significantly curtails the adverse effects of a data breach.
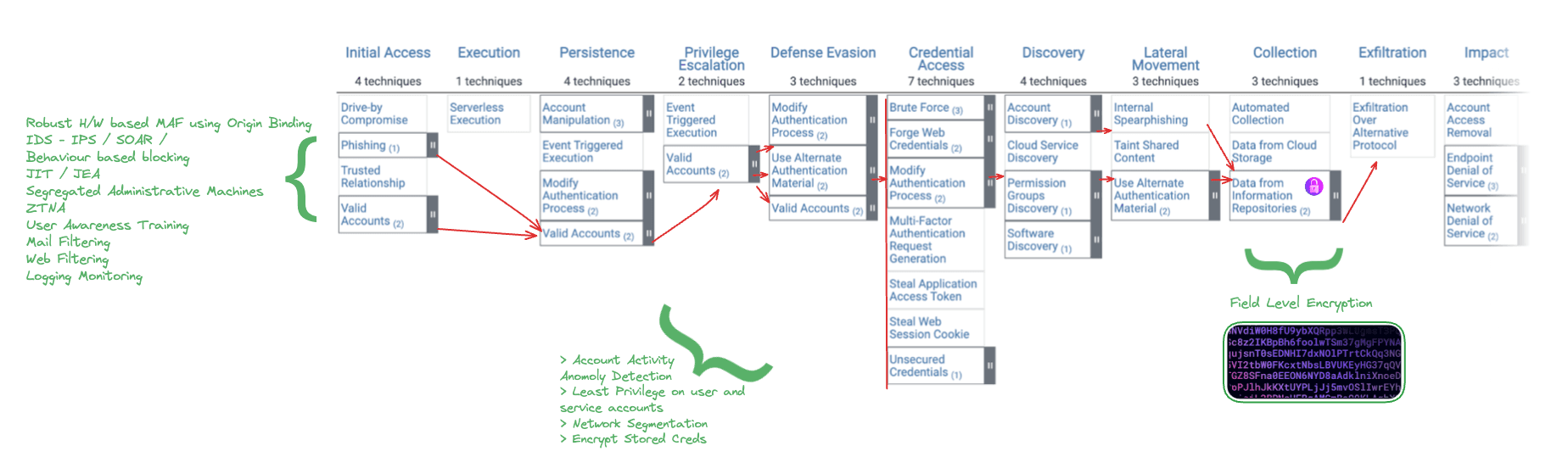
Every organization's risk tolerance varies based on the nature of its operations.
Some may perceive the listed controls as excessive, while others may find them insufficient. Nevertheless, certain foundational controls are universally beneficial for organizations operating in the cloud:
Fortunately, most Cloud Service Providers (CSPs) can enable these controls for a cloud-based infrastructure; you just need the processes to monitor and react to the information once it is presented. It is, however, essential to understand what type of encryption you’re using in your cloud environment.
Many CSPs tout "encryption at rest" through disk-level encryption. Realistically, while this mitigates the risk of a physical attack (disk stolen from a server), it offers practically zero value to a network-based attack, as in the absence of field-level encryption, if the attacker gets access to the database, the information will be in plaintext.
Stay tuned for the next part of our Threat Model series, where we will dissect the threats posed by a Malicious Administrator.