Beyond payment tokenization: Why developers are choosing Evervault's encryption-first approach
How Evervault’s dual-custody encryption model eliminates the fundamental limitations of traditional tokenization for PCI compliance

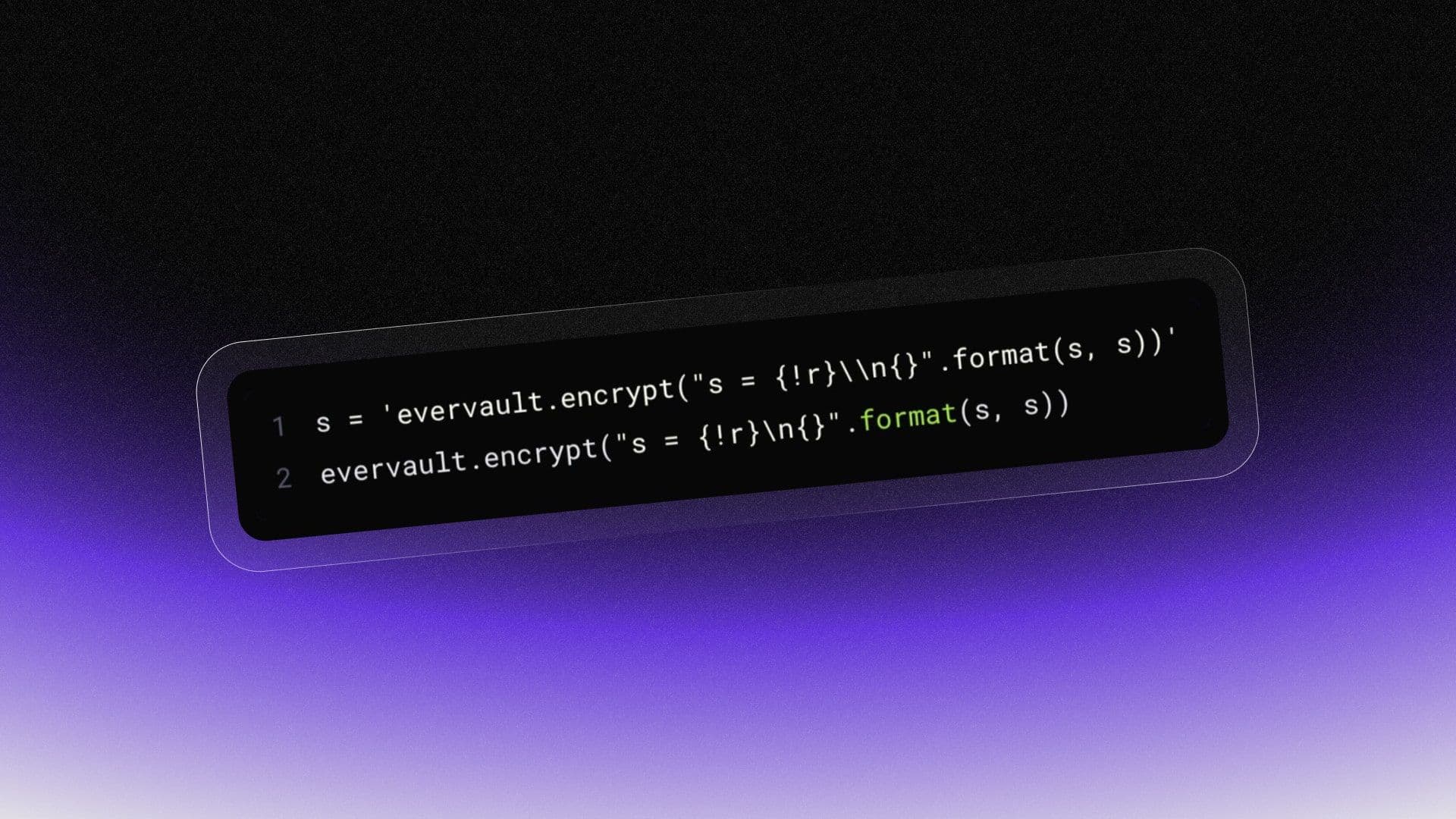
This Python code outputs an encrypted string:
1s = 'evervault.encrypt("s = {!r}\\n{}".format(s, s))'
2evervault.encrypt("s = {!r}\n{}".format(s, s))Such as:
1ev:RFVC:SK38nUPKEtpTwJis:A5jre5DMqvtTpqZN0iEvTPN9wCuMIrDHWWzCpxfPI9x0:
2dYgleJ9sPOnFVyesOCoZX+3AeSg6jDqgQqrL5sPsYxN7w/jvnDJA5lkg0QWnbgH6swuaMQ
38qicWUj8CT5fTPSjNGbc9/8EVgjGh2tPyCeLk+cmIkKdIpsEAhlZVOrOQRK6PLURNV0uLO
4qivlPo2Lmb1Si3g:$Which decrypts to:
1s = 'evervault.encrypt("s = {!r}\\n{}".format(s, s))'
2evervault.encrypt("s = {!r}\n{}".format(s, s))It is the encryption equivalent of a Quine! Built using the Evervault SDK.
If you're interested in encryption, you can sign up for Evervault here.