ASV Scans: What they are, when you need them, and how they work
Learn what ASV scans are, when you need them for PCI compliance, and how Evervault simplifies the process with a modern, user-friendly solution.


Quickly understand your breach reporting responsibility below.
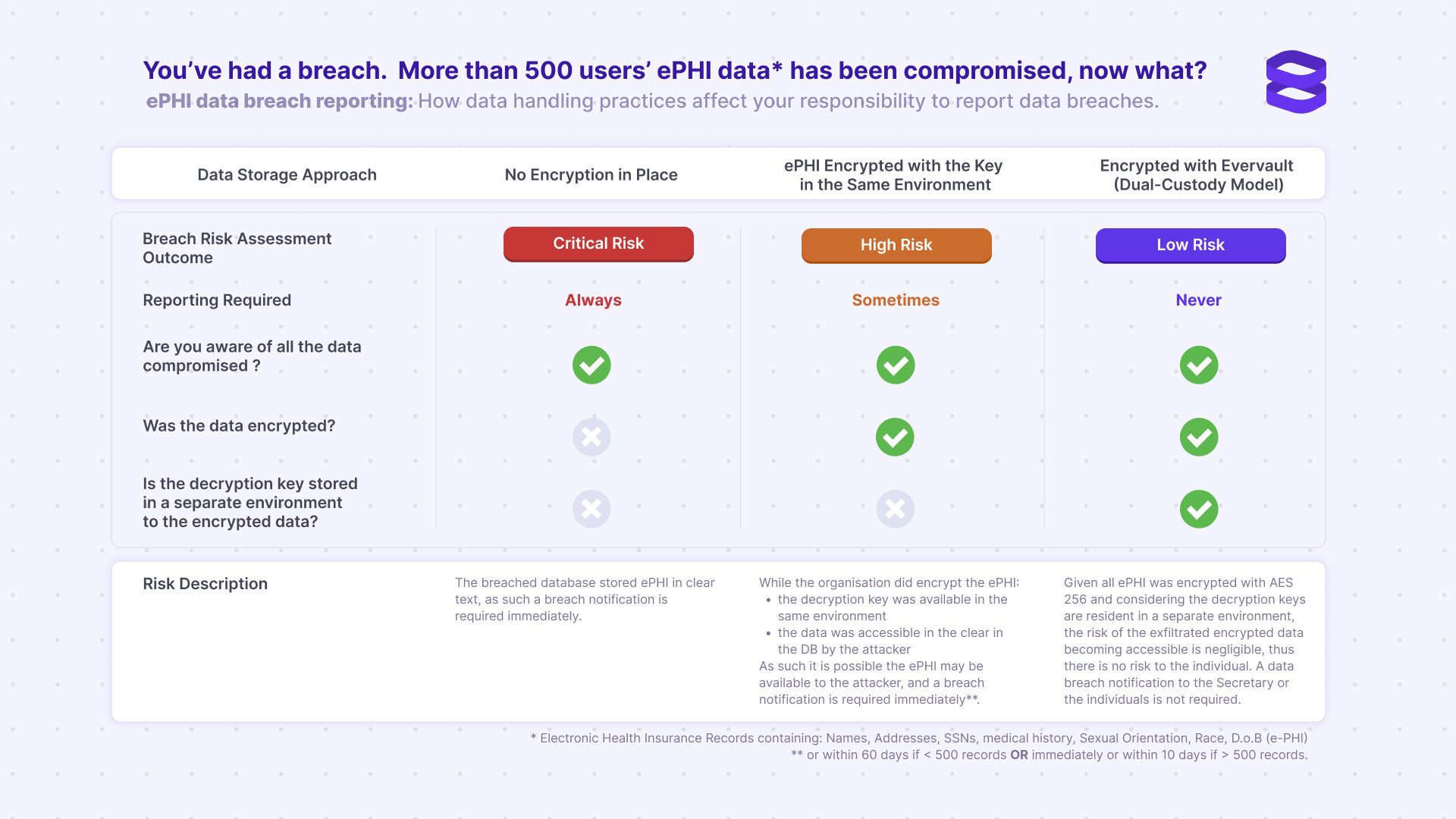
Data breaches can have severe consequences for organizations, including financial loss and reputational damage. For healthcare organizations, data breaches can have even more severe consequences, including legal action, penalties, and loss of trust among patients. As an example, see the list of US companies that have had to publicly disclose their breaches – impacting customer perception and bottom line.
In this guide, we'll help you understand HIPAA compliance, the severity of potential data breaches and your HIPAA compliance obligations in each case. Depending on how your data is protected, you may be legally required to report your breach to the affected individuals, the US Department of Health and Human Services Secretary, and, in certain circumstances, the media. Your breach risk assessment level and reporting responsibility depend directly on your data storage approach. By implementing the safest option, you can better protect yourself and your users.
The Health Insurance Portability and Accountability Act (HIPAA) is a federal law that requires healthcare organizations to protect the privacy and security of patients' protected health information (PHI). HIPAA applies to covered entities, including healthcare providers, health plans, and healthcare clearinghouses. It also applies to business associates, which are third-party vendors with access to ePHI.
HIPAA compliance requirements include implementing administrative, physical, and technical safeguards to protect ePHI. Covered entities and business associates must also have policies and procedures in place to ensure compliance with HIPAA regulations.
HIPAA compliance audits are conducted by the Office for Civil Rights (OCR) to ensure that covered entities and business associates are complying with HIPAA regulations. Audits may be conducted on a regular basis or in response to a breach or complaint.
It's important for healthcare organizations to be prepared for a HIPAA compliance audit by having policies and procedures in place, documenting their compliance efforts, and ensuring that employees are trained on HIPAA regulations.
The severity of a data breach depends on several factors, including the type and amount of ePHI that was breached, the number of individuals affected, and the cause of the breach. The HIPAA Breach Notification Rule requires covered entities and business associates to report a breach of unsecured ePHI to affected individuals, the US Department of Health and Human Services Secretary, and, in some cases, the media.
The breach risk assessment level and reporting responsibility depend on the data storage approach used by the organization. By implementing the safest option, organizations can better protect themselves and their users.

Encrypting sensitive data protects the confidentiality and privacy of protected health information (ePHI) under HIPAA. Encryption plays a critical role in reducing the risk of ePHI breaches and, in most cases, exempts organizations from the requirement to report a breach under HIPAA regulations. When ePHI is encrypted on your server, it is transformed into an unreadable form which can only be deciphered with the relevant key. This process makes it much more difficult for unauthorized individuals to access or misuse the information. It's important to note that not all encryption methods are created equal. Healthcare organizations should use encryption methods that comply with HIPAA regulations and are appropriate for their specific needs.
Evervault makes this easy by providing a platform that allows developers to easily encrypt and process data within their applications without having to worry about the intricate technical details of encryption. This makes it possible for you to secure sensitive information without investing significant resources in developing and maintaining custom encryption solutions. Evervault uses a dual-custody model, meaning we manage the encryption keys for users, eliminating the need for organizations to manage their key infrastructure. As a result, Evervault simplifies the encryption process and makes it accessible to a broader range of organizations, including those without specialized encryption expertise. Since sensitive ePHI never touches your infrastructure in plaintext, it is still protected in the event of a data breach.
Have questions about HIPAA reporting? Feel free to reach out to us to learn more about how to best protect your data.