Beyond payment tokenization: Why developers are choosing Evervault's encryption-first approach
How Evervault’s dual-custody encryption model eliminates the fundamental limitations of traditional tokenization for PCI compliance


Check out what’s new this month at Evervault — New Feature: Card Reveal, revamped solutions pages, and enhancements to Cages.
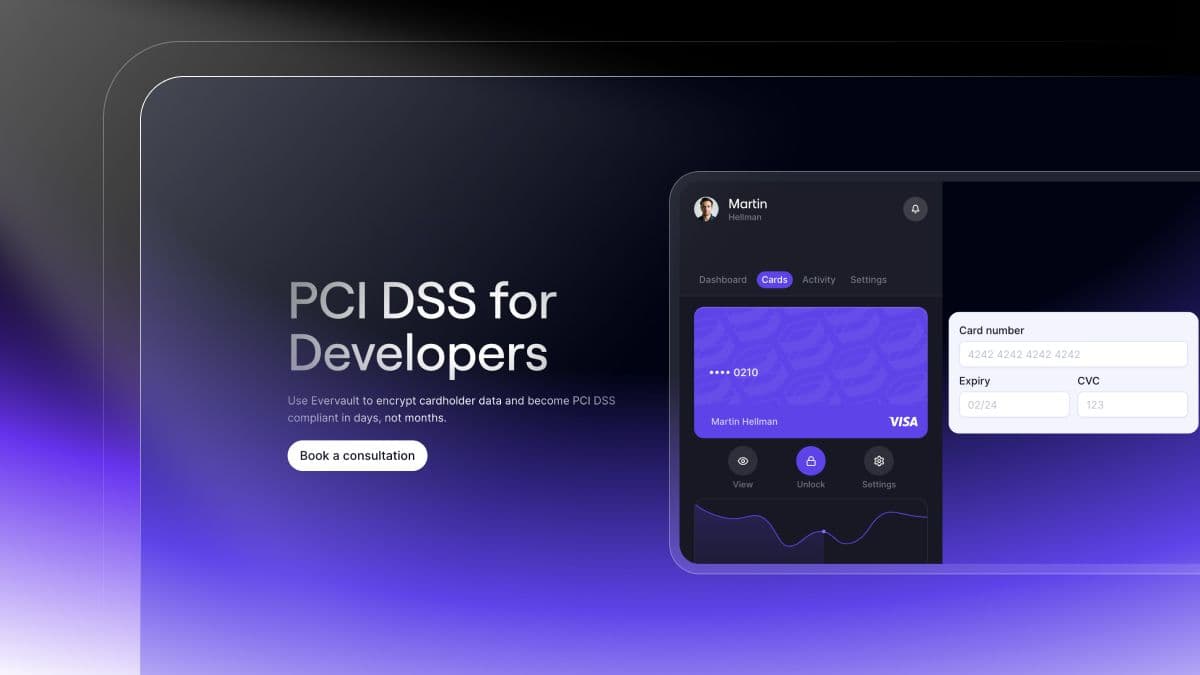
We’ve revamped our PCI Compliance solution to incorporate our newest product features and extended compliance service. Using Evervault to accelerate PCI compliance allows you to collect and reveal cardholder data without worrying about the regulatory and compliance headaches typically associated.
We follow a few simple steps to speed up time-to-compliance:
Learn more about our PCI Compliance solution, or simply respond to this email to book a consultation with our team.
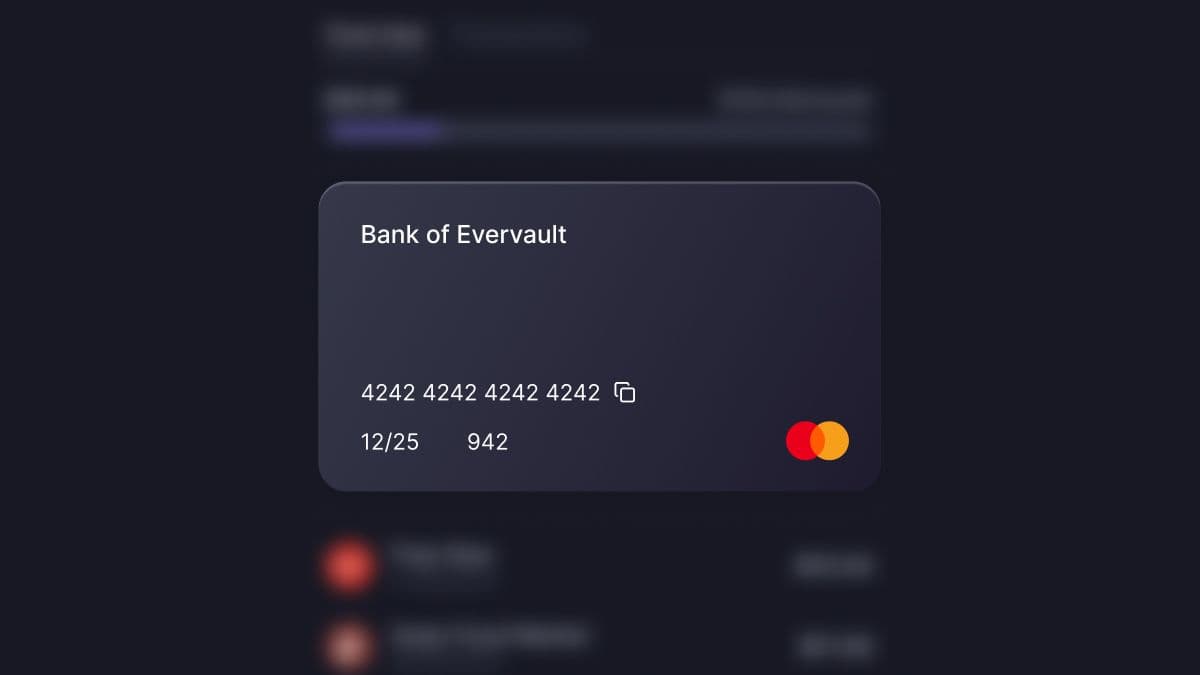
We’re excited to reveal our latest feature: Reveal!
Reveal allows you to display plaintext cardholder data to your end users without increasing your PCI Compliance scope. Evervault-encrypted cardholder data can be passed to Reveal, which is a secure iframe element hosted by Evervault. The resulting workflow means the plaintext cardholder data never touches your infrastructure, which minimizes your PCI compliance scope.
Reveal is fully customizable and can be updated to match your design system with a simple CSS configuration.
To get started, check out the Evervault Reveal docs.
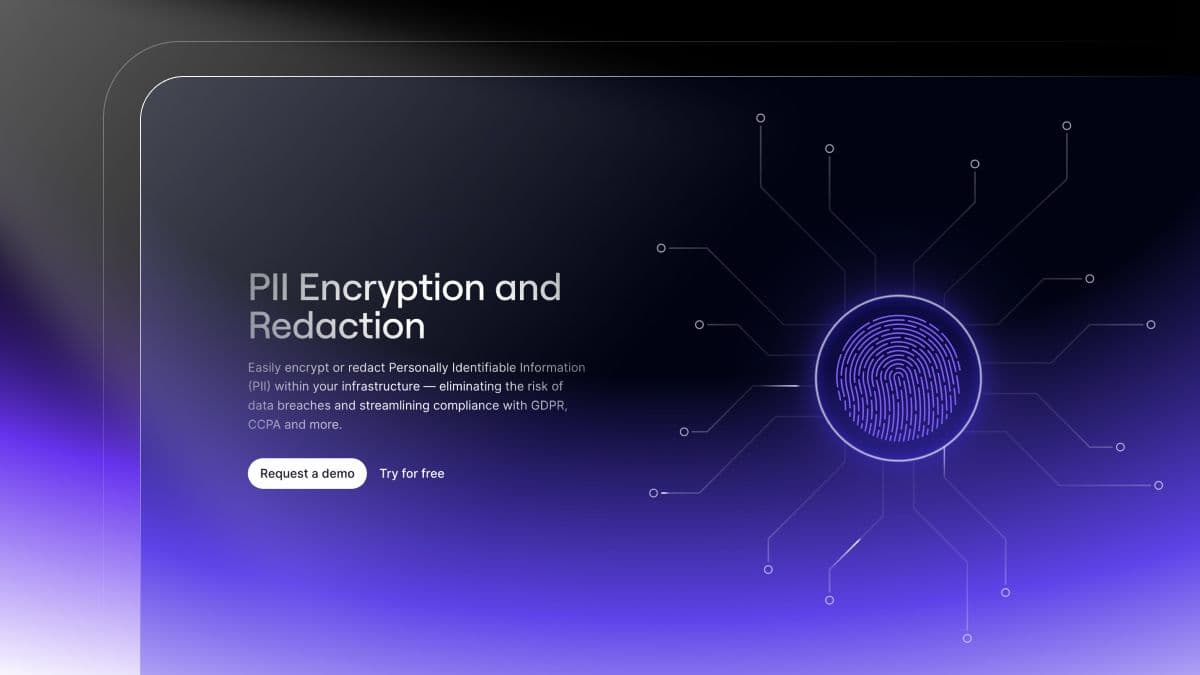
We revamped our PII Encryption solution to better capture the full capabilities of our product. To keep sensitive customer data secure, you can easily encrypt customer PII anywhere in your stack and keep it secured everywhere. Use Evervault to:
Learn more about PII Encryption. Maybe there's an easter egg on the page; who knows.
Trusted Certs
Cages are now issued publicly trusted TLS certs on startup. When your Cage is first deployed, it generates a key pair in the enclave and uses it to create a cert signed by a public CA. This allows you to call your Cage directly from end-user devices (browsers, mobile clients, etc.) without trusting the Cage’s self-signed cert.
The publicly trusted Cage cert will be used for requests to *.cage.evervault.com (note: cage, not cages). The publicly trusted Cage certs are not currently attestable from Evervault Clients (this will be released in the coming weeks).
Trusted headers
Up until now, Cage transaction logs have obfuscated any non-standard, or sensitive HTTP headers. The new trusted_headers option for Cages lets you specify your own allow list of headers to keep in plaintext in your transaction logs. This gives better observability into your Cage responses. For example, you can configure your Cage to expose response error codes and tracing data in your transaction logs:
1trusted_headers = ["X-Error-Code", "X-Trace-*"]You can read more about configuring your Cage’s trusted headers in the docs.
Threat modelling involves understanding the intricacies of your system, identifying vulnerabilities, prioritizing potential threats, and devising proactive mitigation plans. By incorporating threat modelling at the inception of a project, companies can adopt a secure-by-design approach rather than reacting to incidents post-breach.
Check out our content series breaking down potential threat vectors and the methodology behind mitigating them.