Evaluating network tokens: Webinar Q&A
Network tokenization promises better authorization rates, reduced fraud, and enhanced security, but implementing it comes with real questions.


If you're responsible for payments infrastructure, you've probably heard conflicting advice about network tokens. Some vendors promise dramatic authorization rate improvements, while others downplay the benefits entirely. Meanwhile, consultants offer competing perspectives, and it's difficult to find balanced, practical guidance from someone who's actually built these systems.
At Evervault, we're one of the few non-PSPs that have built a standalone network token solution from the ground up. We've helped merchants and service providers implement tokens and migrate from PSP solutions, giving us deep insight into what actually works in the real world. This post distills that experience into a practical evaluation framework you can use to decide if network tokens make sense for your business.
We'll cover the core problems network tokens solve, realistic performance expectations based on real data, how to calculate ROI for your specific situation, and the fundamental trade-offs between different implementation approaches.
This post will not cover what network tokens are and how they work. For that, you should take a look at our previous post: What are network tokens and how do they work?
Before evaluating whether network tokens are worth the investment, it's important to understand exactly what problems they solve. While the payments industry has made significant progress in security and user experience, there’s still a lot of stuff broken, especially for card-not-present (CNP) transactions. They can mostly be broken down into four categories.
Soft declines occur when an issuer rejects a legitimate transaction, even though the customer has sufficient funds and intends to pay. Unlike hard declines, the problem isn't the card itself; it's that the issuer's risk systems are uncertain and block the payment "just in case".
You'll usually see these as decline codes like 05 (Do Not Honor) or 59 (Suspected Fraud). The impact compounds over time: lost revenue from failed legitimate purchases, higher cart abandonment rates, and strained issuer trust that can lower future authorization rates even more.
Hard declines occur when the underlying card is no longer valid. Common causes include expired or reissued cards, lost or stolen cards, and account migrations.
For recurring billing and subscription models, these failures are particularly painful. Payment declines inevitably result in involuntary churn, while the surrounding retry logic and recovery workflows add significant operational complexity and degrade the customer experience. When customers need to update their payment details manually, many simply don’t bother; few people go out of their way to update a card unless they have to.
Even with strong encryption and secure card handling across checkout flows, card-not-present payments remain vulnerable to several fraud vectors. Attackers who acquire real PANs from breaches can attempt unauthorized transactions. Fraudsters often try the same stolen card across multiple merchants (credential replay), and compromised accounts enable card-on-file abuse.
The resulting chargebacks and fraud costs are just the beginning. Chargebacks also reduce issuer trust, which ironically increases the chances of future false declines on legitimate transactions, creating a negative cycle.
Customer experience suffers when payment details fail or need to be re-entered. With PAN-based card-on-file transactions, this happens frequently because PANs expire, are reissued, or get flagged by issuers. Even worse, issuers sometimes require re-authentication of the original PAN using a 3D Secure challenge flow, even when merchant-initiated transactions should continue frictionlessly. (If you’re interested in going deeper down the 3DS rabbit hole, we’ve written extensively about it in the past.)
As a result, customers are forced to update cards mid-subscription, creating friction that feels clunky compared to modern wallet experiences like Apple and Google Pay. This significantly increases the risk of involuntary churn.
Network tokens address declines, fraud, and friction through three core mechanisms: better credential freshness, enhanced issuer trust, and stronger transaction context.
Network tokens improve issuer confidence in several ways. When a network token is provisioned, the issuer has already evaluated the legitimacy of the underlying PAN. Subsequent uses of the token provides the issuer with a second opportunity to approve the transaction, increasing the likelihood of approval compared to when the raw PAN is used for the first time.
Tokens also include additional trust signals: cryptograms, merchant binding, and metadata that provide issuers with more context than a standard PAN transaction. Since the token is cryptographically bound to the merchant (in theory—as we’ve written about previously, this in some cases is more marketing than substance), issuers can reduce false positives and approve legitimate transactions more reliably.
Here's how network tokens address specific decline scenarios:
| Decline Reason | ISO 8583 Code | How Network Tokens Help |
|---|---|---|
| Do Not Honor | 05 | Cryptograms and merchant binding reduce issuer suspicion, converting some declines to approvals |
| Suspected Fraud | 59, 62 | Tokens prove secure CNP transaction origin, lowering false fraud flags |
| Restricted by issuer rules | 57 | Merchant-specific token confirms the transaction is intended for this merchant |
| Invalid transaction conditions | 12, 91 | Tokens carry richer metadata, reducing blanket risk rules |
Tokens are automatically updated via the card schemes' lifecycle management services, so merchants maintain a current, valid credential without manual intervention. This eliminates declines due to expired, replaced, or reissued cards.
Lifecycle updates include:
The result is fewer hard declines and higher approval rates, which is especially valuable for card-on-file and subscription models.
Network tokens reduce the risk of online payment fraud by replacing the PAN and binding tokens to specific merchants and contexts.
| Fraud Vector | How Network Tokens Reduce Risk |
|---|---|
| Stolen PANs | Tokens are merchant-bound* and domain-bound**. If a token is stolen for one merchant, the scheme can block that token without affecting tokens tied to the same PAN at other merchants. Network tokens also can’t be typed into a standard checkout form, so attackers would need to use their own PSP integration, which is unlikely. |
| Replay attacks and credential stuffing | Token cryptograms are cryptographically bound and single-use, preventing reuse across merchants. |
| Account takeover and card-on-file abuse | Tokens protect the underlying PAN and can be suspended or revoked quickly; meaning issuers can block suspicious activity. |
*A merchant-bound network token is tied to a specific merchant ID (MID). It can only be used for transactions processed by that merchant.
**A domain-bound token is tied to a specific device, browser, or app domain. It can only be used within that same technical environment.
It's important to note that tokens don't prevent all fraud, but they limit exposure to a single merchant's token rather than the underlying PAN.
Additionally, network tokens give the issuer a second chance to run a risk analysis on a transaction rather than just a point-in-time authorization with a raw PAN. They can run a risk analysis when the token is created, and when a cryptogram is generated for a subsequent transaction. This gives them a much greater surface area to build a stronger risk profile for a given transaction.
The lifecycle management capabilities mean recurring payments continue without interruption. Customers don't need to manually re-enter card details after expiry or reissue. This reduces failed payments, abandoned subscriptions, and checkout friction compared to PAN-only workflows.
Card networks like Visa and Mastercard are moving toward near-universal adoption of network tokens. Mastercard, for example, has signaled plans to phase out manually entered PANs by 2030, with the future of payments dominated by Click-to-Pay, digital wallets, or maybe even agentic tokens.
Based on realtime data we’ve gathered from live transactions at Evervault, our analysis of global network token requests shows that approximately 89.9% of attempted tokenizations are fully supported by issuers, although a portion of these may still be declined for other reasons. Around 10.1% of attempts fail because the issuer does not yet support network tokens. Variance between countries was also smaller than expected, however, there were some countries without any successful network token volume.
| Afghanistan | Anguilla | Burkina Faso | China* |
| Comoros | Cook Islands | Djibouti | Equitorial Guinea |
| French Polynesia | Haiti | Holy See | Jersey |
| Nepal | Niger | Russian Federation* | Sierra Leone |
| South Sudan | Suriname | Tonga | Turkmenistan |
| United States Minor Outlying Islands | Yemen |
*China (only on Visa and Mastercard rails, excluding e.g., China UnionPay)
*Russian Federation (only on Visa and Mastercard rails, excluding e.g., Mir)
Even though network tokens are widely supported, adoption is not uniform across issuers or countries. To operate reliably, you should:
Key takeaway: Network tokens are increasingly standard and provide clear benefits, but inconsistent adoption means a fallback strategy using PANs, combined with monitoring and routing logic, is essential for reliability—especially for card-on-file and subscription use cases.
Real-world example: South African PSP Stitch Money saw their network token usage jump by 40% overnight when their largest acquirer started supporting network tokens.
Network tokens can increase authorization rates, reduce fraud, and lower transaction fees. The actual benefit depends on your transaction volume, average transaction value (ATV), and operational costs, but you can use simple blended benchmarks to estimate ROI.
We've combined public performance data for Visa and Mastercard to give a single illustrative benchmark:
| Network | Auth Uplift | Fraud Reduction |
|---|---|---|
| Visa | 4.6% | 40% |
| Mastercard | 3.0% | 50% |
Using a global average card mix (Visa 60%, Mastercard 40%), the blended numbers are:
You can adjust these if your business has a different card mix—more Visa or Mastercard transactions will slightly change the blended percentages.
Revenue uplift comes from additional transactions approved due to network tokens:

Example:
100,000 × $50 × 0.9 × 0.0396 ≈ $178,200
Fraud savings result from fewer chargebacks and lost revenue:

Example assumptions:
100,000 × $50 × 0.01 × 0.44 × 1.25 ≈ $27,500
Interchange and processing benefits:
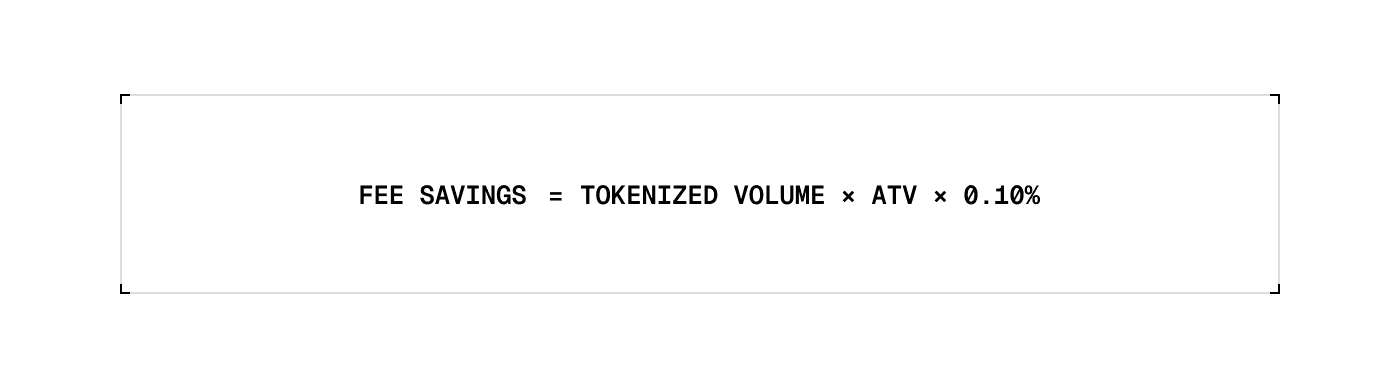
100,000 transactions × $50 × 0.1% ≈ $5,000

When measuring the ROI of network tokens, start with an accurate baseline. Many PSPs may already be using network tokens behind the scenes (and they’re probably charging you for it!), so it's important to ensure your benchmarks reflect truly non-tokenized transactions. Otherwise, you risk overestimating the incremental benefit of adopting network tokens.
For the blended average authorization uplift of 3.96%, roughly 2.5% of that gain typically comes from reducing hard declines. This improvement is driven by automated lifecycle management, which keeps card credentials current. However, you won't see the full effect immediately; it accumulates over time as cards naturally expire, are reissued, or replaced due to loss or fraud. As a result, you’ll need to be patient with analysing the impact of network tokens. Don’t expect any material impacts for at least 3-6 months.
When you start exploring network tokens, you'll quickly realize there are three main ways to implement them:
Option three is rare and only viable for the very largest merchants and PSPs, but it's worth understanding so you can see where the trade-offs come from.
Before comparing specific approaches, it’s important to understand these six factors that determine which model will work for your business.
1. Token Portability
Can the token be used across multiple PSPs or acquirers, or is it locked to a single processor? Portability matters if you ever want to do multi-PSP routing, switch PSPs, or avoid recollecting cards in the future.
2. TRID Ownership (Token Requestor ID)
Who owns the scheme-level relationship with Visa, Mastercard, and Amex for requesting and managing tokens? If you own the TRID, you can directly control lifecycle management (updates, refreshes, expirations). If your PSP owns it, you're dependent on them. Network token migrations, while technically possible, are an enormously painful process. Most merchants simply opt to create all of their network tokens from scratch.
3. Routing Control
Do you decide where to send transactions, or does your PSP? With routing control, you can direct traffic to the processor with the best cost or performance profile for a given card, issuer, or region. Without it, you take whatever your PSP decides.
4. Visibility and Reporting
Can you see whether a given transaction used a token or a PAN? Do you know when a token was updated, expired, or failed? Without visibility, you can't debug failures, measure ROI, or prove compliance with mandates like Visa's EU tokenization incentives (or rather, disincentives for not using tokens).
5. Cost Efficiency
Do you need to pay multiple times to tokenize the same card (e.g., once per PSP), or can you tokenize once and use that token everywhere? Costs also include ongoing per-transaction token usage fees.
6. Compliance and Regulatory Readiness
With mandates starting to roll out, especially in the EU, are you in a position to prove that you're applying tokens where available? If your PSP doesn't disclose token usage, you may be unnecessarily penalized or overcharged without realizing it.
Pros:
Cons:
Best for: Merchants who plan to stay with one PSP and want the simplest possible implementation.
Pros:
Cons:
Best for: Merchants who want multi-PSP flexibility, operate recurring or subscription models, or seek more control and visibility over how tokens are used.
All of the major card networks offer token services directly (Visa VTS, Mastercard SCoF, Amex AETS). In theory, you can integrate with them yourself.
Pros:
Cons:
Best for: Only the very largest merchants have the resources and appetite to manage network tokenization as a core competency.
| Factor | PSP Solution | Standalone Solution | Build In-House |
|---|---|---|---|
| Token portability | ❌ No | ✅ Yes | ✅ Yes |
| TRID ownership | ❌ PSP owns | ✅ You own | ✅ You own |
| Routing control | ❌ PSP decides | ✅ You decide | ✅ You decide |
| Visibility & reporting | ❌ Limited | ✅ Full | ✅ Full (but you must build it) |
| Cost efficiency | ❌ Duplicate tokens per PSP | ✅ Tokenize once | ✅ Potentially cheapest at scale |
| Compliance readiness | ❌ Risky (opaque reporting) | ✅ Strong (you see usage) | ✅ Strong (but your burden) |
| Complexity | ✅ Simple | ⚠️ Moderate | ❌ Very high |
We've covered the fundamentals of network token evaluation, but there's much more to explore around implementation best practices, real-world performance data, and navigating the evolving regulatory landscape.
Watch Shane Curran, Evervault CEO, cover these topics in depth and answer attendees' questions about network tokens.
Our on-demand webinar covers: